The University of North Texas is committed to promoting development and assisting faculty and staff in pursuing higher education for themselves and their dependents. To see the full policy, look here.
FAQs
The window server directories employees are supposed to acces are the following:
- \\citcwin1.unt.ad.unt.edu (Apps, Develop, Documentation, Scanner, Software)
- \\citcwin2.unt.ad.unt.edu (CRSDT, Home, Shareddocuments, Telecom)
- \\filehub.admin.unt.edu (CCAIM, EISTS, Oracle, Psft_Attach, Shared)
Yes! However, the CPE is specific to security certifications.
The management at Barnes and Noble has instructed us that to get educational discounted prices, the UNT community members need to go to: here. This site is a partnership with Barnes and Noble and offers many of the same software at the same discounts as one used to be able to purchase off the shelves in the old Union bookstore. You will also notice that by clicking on their hardware tab that they have discounted hardware as well.
The University of North Texas has an agreement with Dell Computer which provides special educational purchase opportunities for UNT faculty, students and staff. Please see the Dell Education Sales site.
No. You can view each short video over as many sessions as required. You do not need to complete the training in one session because your progress will be saved when you exit the training site.
No. The FERPA training module included in the Securing the Human training is meant to enhance rather than replace, any existing FERPA training.
Employees should login to https://my.untsystem.edu, and click on the link in the Information Security Training box.
Click Start, and then click Devices and Printers. On the top panel, click Add a printer. In the dialog box, select “Add A Network, Wireless, or Bluetooth Printer”. At the bottom of the dialog, select “The Printer That I Want Isn’t Listed”. Select the bullet “Find A Printer In The Directory, Based On Location or Feature”. This will bring up a list of all printers in Active Directory. To narrow down the search to strictly printers in ITSS, type CITC into the Name field and click Find Now.
On your Outlook client, click on File, Account Settings and Delegates Access. On the Delegates window click on Add, highlight the user, click on Add and OK. You will then be able to edit the delegate permissions for your mailbox.
Open Outlook. Click File and then click Account Settings button and select Account Settings from the drop down menu. Select the Data Files tab and click the Add button. Navigate to your .pst file and click OK. You should now see your archive listed in the mail panel on the left.To create a new archive folder, navigate where you want to save the .pst file and type in a new name in the File Name field and click OK.
Please go to https://ams.unt.edu and follow through the instructions after singing in. After changing your password, make sure to input the new password on your mobile device and other devices where you have your old password stored. As this may run a risk where your account can be locked out because of multiple authentication failures.
In some situations you might identify you need to create a separate document library that resides outside your OneDrive for Business folder.
Office 365 allows you to accomplish this task in just a few steps:
- First, login to here.
- Then, on the top right corner the page click on the settings icon and select "Add an app" from the drop down menu.
- Then, click on the "Document Library" app icon listed under Noteworthy.
- On the popup menu, type a name for your library (avoid including spaces), and click create.
- Then on the top right corner of your newly added library click on the three dots to change its settings.
- Then, click on the “library tab” of the newly created library and then click on “library Settings”
- Then click on Permissions for this document library.
- Then click on "Stop Inheriting Permissions" and click ok.
- By default Everyone except external users will have access to this library for collaboration purposes.
- However, if the use case requires differently, you can check this group and remove as needed. Then, click "OK" on the confirmation box and you're all set with permissions.
- To access the newly created library click on your recent items list.Click on Sync, if you would like to sync with your computing device.
Click Start, and then click Run. In the open box, type cmd and then click OK. In the command prompt, type ipconfig /all. Your IP is located under “IP Address” and MAC is located under “Physical Address”
Click Start, and then click Computer. On top of the window, click Map Network Drive. Select a letter drive and type in the full path provided by your immediate manager in the Folder field. For example \\citcwin1.unt.ad.unt.edu
Any employee can create a standard configuration quote. It is best to involve your local IT staff in the generation of the quote since they can help you determine the appropriate standard configuration and accessories for your needs. This will also prepare them to configure and install the machine when it arrives. Please go to the ITSS Standard Configurations page and follow the instructions there: http://itss.untsystem.edu/divisions/mrs/policies/hardware
To recover an older version, please see the instructions here.
You can fix sync errors you get while using the OneDrive for Business sync app by choosing View sync problems in the OneDrive for Business menu. The error dialog recommends solutions for each sync error.
If you suspect a security violation has occurred, contact your IT Helpdesk right away. If confidential or sensitive data is associated with any computer involved in the incident, please call Information Security immediately at 940-369-7800 or contact us by email at security@untsystem.edu.
Refrain from accessing or further interacting with the computer in question. This will help preserve evidence integrity before the Information Security team can collect an image for forensic analysis.
Incident Reporting Steps:
- Notify your IT Helpdesk or IT support staff
- Notify your immediate supervisor
- Do not allow any changes to be made to the computer or related system.
UNT UIT Helpdesk 940-565-2324
HSC Helpdesk and Client Services 817-735-2192
UNT Dallas ITSS Helpdesk 972-780-3626
UNT System CTSS Helpdesk 940-565-4078
If you wish to report criminal activity, contact your campus Police Department.
UNT Police Department 940-565-3000
HSC Police Department 817-735-2210 (non-emergency number)
UNT Dallas Police Department 972-780-3009
More information is available at Incident Reporting.
E-mail Information Services with the employee’s name, EMPL, title, and the badge access requested. An IDO will be prepared for the new employee to take to ID Systems to pick up the badge. The IDO will be placed in the new employee’s box.
E-mail Information Services with the employee’s name, EMPL, title, and the keys requested. A key request will be sent to Access Control and a letter detailing how to pick up keys will be placed in the new employee’s box.
E-mail Patricia Bell and notify her that you need a new badge. Please include your EMPL Id. You will receive an IDO to take to ID systems on the UNT campus where your new badge will be printed.
Request the form by e-mailing ITCompliance@untsystem.edu. A written agreement must be in place between the institution and the individual for whom the EUID is requested.
This topic describes how to configure your desktop applications to work with Office 365.
You can request help from your IT support group here.
Alternatively, this article describes problems you may have using the OneDrive for Business sync app, and offers solutions or workarounds.
To make a document or folder private, you can stop sharing it.
-
Select the people icon for the document or folder to open the Share dialog box.

-
In the Shared With dialog box, select Can view or Can edit next to the person you want to stop sharing with, and then select Stop sharing.

For more information on this topic here
You must have the OneDrive for Business sync app available here.
To turn Delve off click on your Office 365 Delve settings icon and select "Turn on or off" .

Click OK to confirm:

The videos linked below show you how to upload a file, upload several files at once, and how to quickly create new Office documents in your OneDrive for Business library.
All employees should complete the training by Wednesday, November 13, 2019. Employees who do not complete the training by this date are at risk of losing access to computer resources.
The length of all of the required videos in the training is about 48 minutes. All videos have a one-question assessment at the completion. There is also one page of information to read after the “You Are the Shield” segment.
Contact your local help desk or IT support team:
UNT UIT Helpdesk:
http://it.unt.edu/helpdesk
helpdesk@unt.edu
940-565-2324
UNT HSC Helpdesk:
http://helpdesk.hsc.unt.edu
helpdesk@unthsc.edu
817-735-2192
UNT Dallas Helpdesk:
https://oit.untdallas.edu/help-desk
helpdesk@untdallas.edu
972-338-1448
UNT System Service Desk
ITHelp@untsystem.edu
940-565-HELP (4357)
While you are in Remote Desktop, you will need to use the following keystroke command CTRL+ALT+INSERT
Once inside the training system, click the “Contact Support” link to the left of the training videos. You can then send an email to training@security.untsystem.edu describing your difficulty to the security support team. Or you can contact your local help desk.
Before you can click the tick-box, you must navigate to the URL. Once you return to the training, you will be able to click on the acceptance statement.
UNT System did not purchase any addition language training packages, therefore, the training is only available in English for employees of the UNT System institutions.
Contact training@security.untsystem.edu about the problem to get this resolved.
UNT System does not restrict employees from using mobile devices unless confidential information is involved. Confidential information may not be stored on mobile computing devices, i.e., laptops, tablets, smart phones, etc., unless the device is encrypted. Cloud storage services are available through One Drive for Business. Employees may use OneDrive for Business to store files for a UNT System institution business purposes only. For more information about encryption and other topics on information security, please see the UNT System Information Security Handbook section 12.4 for information about encryption.
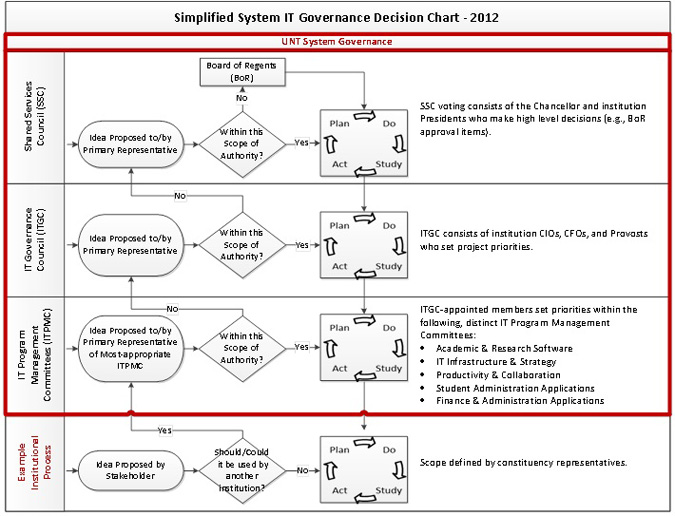
Governance Decision Process Guidelines
The chart below identifies the overall process of governance between institutional decision-making and IT Shared Services decision-making. It is important to understand that campuses will continue to make technology decisions for their own needs unless the project rises to the level of potentially being a shared service. The answer to the question "should/could this be used by another institution?" determines whether or not a decision needs to rise to the Shared Services Governance Process. In that instance, the campus process will shift to the appropriate PMC to make a shared/not shared decision. Should the PMC decide the project should be shared service then the IT Shared Services Governance Process will be used for decision making relative to it. If the PMC decides that the project is not a shared service then the project will immediately be returned to the originating campus to address as that campus sees fit.
All workstations should use antivirus software for protection against malware. ITSS Information Security provides McAfee Antivirus software that can be downloaded at AntiVirus Download with a valid EUID and password. The antivirus software should be configured for regular updates and automatic scans to remain effective. In addition, you can reduce your risk of compromise by following these practices:
- Keep all software up to date.
- Backup your data.
- Download files and applications from trusted sources only.
- Be wary of hyperlinks in emails and only click on links you expected to receive.
You can learn more about information security by visiting the Information Security website here.
Any classification of data can be stored in OneDrive for Business, however it is not the appropriate storage location for institutional records.
Data classification/categorization information can be found in the Information Security Handbook, under section 7.3.
In general, storage of information must adhere to institutional policies and standards for protecting information, including physical security. The protection of information must be commensurate with the value of the information (e.g., category I requires the highest level of security, therefore no unauthorized sharing, access, or use of the information is allowed).
In regard to the exchange of information:
- Services provided by a third-party must adhere to institutional requirements for protecting information. Microsoft meets this requirement with their implementation of OneDrive for Business.
- Information exchanged within the institution must be done in a secure manner.
In regard to mobile devices:
- All institutionally owned laptops must be encrypted, and category information can be stored on mobile devices as long as encryption technology is enabled on the device. If no encryption is in place the information cannot be stored on the device.
In regard to backups:
- Backup processes must protect the confidentiality, integrity and availability of stored information.
In regard to who can store information, it is up to the information owner to make that decision, as they approve access to their information. Users must adhere to institutional policies and standards for protecting information when accessing resources and information remotely.
In summary, regardless of the technology used to store information, institutional policies and standards must be followed to ensure its protection.
Campus Technology Support Services, It Service Management, Communication and Collaboration Services, Enterprise Systems Infrastructure Services.
We intend to review processes to ensure that we are taking maximum advantage of current PeopleSoft capabilities. Our current system is basically using the functionality available 10 years ago when the original implementation occurred. The goal of process reviews is to minimize customizations which drive up the cost of the upgrade and ongoing support.
Oracle requires us to physically split the Human Capital database from the Campus Solutions database. Currently, this data is in one physical database. In addition to the split, we will be upgrading both Human Capital and Financial systems. In addition, we will implement three new modules in the Human Capital system:
- ePerformance
- Talent Acquisition Management
- Candidate Gateway
We will be implementing one new module in the Financial system:
- eSettlements
Finally, as part of the upgrade project, our portals will be redesigned for “look and feel” to improve the user experience.
A content management system used widely through UNT.
Delve helps you discover the information that's likely to be most interesting to you right now - across Office 365.
The more you and your colleagues work together, by viewing, editing and sharing each other's documents, the more useful Delve will be for all of you.
Delve learns from how you and your colleagues work, and tailors the information to each of you. What you see in your views in Delve is different from what your colleagues see in theirs.
Delve never changes any permissions, so you'll only see documents that you already have access to. Other people will not see your private documents, for example documents that you've stored in private folders in OneDrive for Business.
You don't have to remember the title of a document or where it's stored. Delve shows you documents no matter where they are stored in OneDrive for Business or in Sites in Office 365.
You can find more on Delve here.
OneDrive for Business is a place where you can store, sync, and share your work files across multiple devices. The files you store in OneDrive for Business are private, unless you decide to share them.
Total contracted project cost is $5,011,347.
It is the quickest and easiest way to share a file with everyone in the organization and allow edits unless you change the default permission setting.
It is important to note that the "Shared with everyone folder is not a common repository. It is your personal folder you share with everyone in the organization.
In Delve you'll find Word, PowerPoint, Excel, and PDF documents - that are stored in OneDrive for Business, in Sites in Office 365, or that have been shared with you as attachments in emails. You may also find videos* that have been uploaded to Office 365 Video.
You'll only see documents that you already have access to. You will not see documents that are stored in private folders unless they're shared with you.
Documents and videos are shown as content cards surfaced on different views. To learn more about the content cards, see How to use the content cards in Delve and What kind of information will I find in Office Delve.
Information Security offers online security awareness training for faculty and staff of all UNT System components. The security awareness course covers the basics of information security, as well as current trends, best practices, and important policies regarding computing usage throughout the UNT System. Full-time faculty and staff will be assigned training through the SANS Institute Securing the Human online video tutorials. After access has been granted, full-time employees can login with their UNT System credentials at here. For more information about the training, see Security Frequently Asked Questions page. Part-time employees, including student employees, can continue to access training here. Please note that accessing this training through Firefox or Chrome will require using the domain\username when logging in.
If you clicked on a link or responded to an email that you suspect may have been a phishing attempt, you should immediately change your password and contact your IT support staff. The senders of the fake email may be attempting to collect valid credentials for access to UNT institution services, or may have installed malware on your computer. Report the incident to your supervisor and IT support staff, so any additional containment or handling can be coordinated.More information is available at https://itss.untsystem.edu/security/phishing
A functional upgrade. That means we will review business processes to take advantage, to the greatest extent possible, of functionality in PeopleSoft version 9.2. This type of upgrade has not been done since the implementation of PeopleSoft 10 years ago. It will involve users deeply in the upgrade. All previous upgrades have been “technical” in nature – basically upgrading the engine but minimizing any impact on existing business processes. Specifically, a functional upgrade means we will be doing:
- Application functionality fit-gap sessions
- Business process analysis
- Replacement of customizations with newly delivered functionality
- Implementation of new modules
End-user data should be stored in OneDrive for Business. Official university records should not be stored on OneDrive for Business.
The project starts June 2013. It is planned to end in September 2015. The basic upgrade, however, will be completed by July 2015.
After an exhaustive review of all potential alternatives, the consensus decision was to move forward with a PeopleSoft functional upgrade. The decision process involved:
- Individuals from campuses
- Four separate discussions with the IT Governance Council (comprised of the 3 campus Chief Financial Officers and Provosts, Vice Chancellors for Finance and Academic Affairs and Student Success, and campus CIOs)
- Two discussions with the Shared Services Council (Chancellor and 3 University Presidents as well as CFOs and Provosts) resulting in an approval to move forward with a functional upgrade.
- A discussion with the Board of Regents and final approval by the Board of Regents at their May 16, 2013 meeting.
Use this contact form to message us.
Campuses are funding the upgrade based on the IT Shared Services Cost Allocation formulas. Project funding actually occurs over 4 fiscal years – a small amount in FY2013, the largest amount in FY2014, a smaller amount in FY2015 and some in FY2016.
All employees and contractors of UNT, UNT Dallas, and UNT System are required to complete Security Awareness Trainining. Employees who were hired before January 1, 2019 and have completed training through the onboarding process have already met this requirement.
Through an RFP process, we have selected Ciber Inc. to provide the skills needed to upgrade our PeopleSoft systems. Also, they are providing professional project management for the project. Internally, we will have our own project coordinator working closely with the Ciber Project Manager. ITSS EIS staff will be assigned to the project and will perform technical aspects of the upgrade.
Keeping our confidential data secure requires the effort of technology, processes and people. In this training, you will learn why you are an important part of information security and what you can do to protect data. In addition, many regulations and standards require security awareness training for every employee.
Because Oracle will drop support of our current Financials and Human Capital software version in July 2015. Support includes many updates necessary to carry on business effectively. We must upgrade from our version 9.0 to version 9.2 to retain support. Campus Solutions will remain at version 9.0.