8.1. Threat Intelligence Support
Threat Intelligence support to the acquisition process provides an understanding of foreign threat capabilities that is integral to the development of future U.S. military systems and platforms. Identifying projected adversarial threat capabilities, to include scientific and technical developments, which may affect a program or a capability’s design or implementation is crucial to a successful development process. Furthermore, the applicable threat information must be continually updated to account for adversarial capabilities throughout the program or capability’s projected acquisition to ensure that technological superiority over adversarial capabilities is maintained. See the graphic in Figure 8.1.F1.
Figure 8.1.F1. Depiction of Life-Cycle Intelligence Analysis Requirements
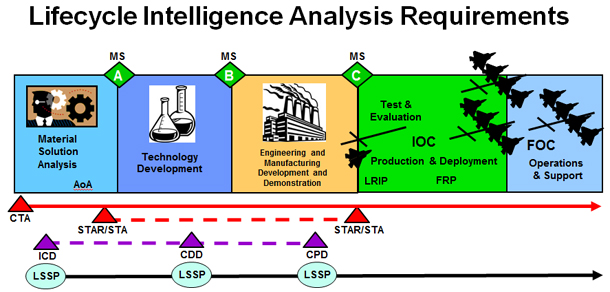
Figure 8.1.F1 illustrates the range of support provided by the threat intelligence community over the life of a particular capability shortfall identification process and resulting system acquisition program. Capstone Threat Assessments (CTA) inform the capability shortfall identification process as well as during early phases of system acquisition prior to the generation of a STAR/STA. The CTAs project foreign capabilities in particular warfare areas looking out 20 years.
At the beginning of the Material Solution Analysis phase, the program office or capability sponsor should contact the appropriate intelligence production center to support integration of validated threat information into the Technology Development Strategy. Threat information may come from DIA-validated Capstone Threat Assessments or other DIA/Service validated STARs/STAs that align with the capability mission, CONOPs, and employment timeline.
Once the capabilities sponsor, program manager or other appropriate enabler identifies concepts or prototypes for the materiel solution, the program office or capability sponsor should task the appropriate intelligence production center for the lead service to produce the System Threat Assessment Report (STAR) for Acquisition Category (ACAT) I/ Major Defense Acquisition Programs (MDAPs) and the System Threat Assessment (STA) for ACAT II programs in accordance with the regulations of that service. The program office needs to work with the producing intelligence center to provide system specific characteristics, employment CONOPS, and employment timeline as they evolve. The program office must also work with the appropriate Service Intelligence Production Center to identify Critical Intelligence Parameters (CIPs) and ensure production requirements are levied against those CIPs.
Analytic Baseline. A system's Analytic Baseline is comprised of DoD-level authoritative policy planning guidance and an intelligence assessment of present trends, patterns and conditions, combined with validated parametric, characteristics/performance and employment data needed for development, testing, and/or training. When combined with information on appropriate friendly and neutral (Blue/Gray/White*) systems, it represents an extrapolation of the total security environment in which the system is expected to operate. A package comprises a scenario, concept of operations, and integrated data used by the DOD components as a foundation for strategic analyses. Examples of analytical baselines include scenarios and supporting data used for computer assisted war games and theater campaign simulations.
* The three colors reflect three different entities. Blue represents U.S. system data, Gray represents U.S.-produced but foreign-operated system data, and White represents neutrals. When doing long-term analysis, the impact of Blue systems must be taken in light of friendly and neutral systems.
8.1.1. Capstone Threat Assessment (CTA)
CTAs provide the bedrock analytical foundation for threat intelligence support to the defense acquisition process. CTAs, covering major warfare areas, present the DoD Intelligence Community validated position with respect to those warfare areas and will constitute the primary source of threat intelligence for the preparation of Initial Threat Environmental Assessments, STARs/STAs, and threat sections of documents supporting the JCIDS process. In order to effectively support both the capability development and acquisition processes, CTAs are not specific to existing or projected US systems, cover the current threat environment, and, in general, project threats out 20 years from the effective date of the CTA. With the lead intelligence production center, DIA's Defense Warning Office (DIA/DWO) co-chairs the Threat Steering Group (TSG) that produces and reviews the document. CTAs should be updated as determined by the responsible TSG but in any case every 24 months. DIA validates all CTAs.
Table 8.1.1.T1. Listing of Capstone Threat Assessments
|
WARFARE AREA
|
PRIMARY PRODUCTION OFFICE OR CENTER
|
|
Air Warfare
|
National Air and Space Intelligence Center (NASIC)
|
|
Chemical, Biological and Radiological Defense
|
Defense Intelligence Agency (DIA)
|
|
Information Operations
|
DIA/Joint Information Operations Threat Working Group
|
|
Land Warfare
|
National Ground Intelligence Center (NGIC)
|
| |
|
|
Missile Defense
|
Defense Intelligence Agency (DIA)
|
|
Naval Warfare
|
Office of Naval Intelligence (ONI)
|
|
Space Warfare
|
National Air and Space Intelligence Center (NASIC)
|
|
The Capstone Threat Assessments can be found at the JWICS or SIPRNET websites of the primary production office or center.
For more information contact DIA’s Defense Warning Office at:
JWICS email - dise541@dodiis.ic.gov
SIPRNET Email – jeffery.vales@dse.dia.smil.mil
Commercial – 434-956-2170
DSN 521
|
8.1.2. System Threat Assessment Report (STAR)/System Threat Assessment (STA)
The Defense Intelligence Agency (DIA) provides validation for System Threat Assessment Reports (STARs), prepared by the appropriate Service, to support Acquisition Category (ACAT) ID/ Major Defense Acquisition Programs (MDAPs). Appropriate Defense Intelligence organization(s), identified by the component headquarter intelligence organizations, prepare the STAR. The assessment should be kept current and validated throughout the acquisition process. DoD Instruction 5000.02 requires that MDAPs have a validated STAR in place at Milestones B and C (and at program initiation for shipbuilding programs). The assessment should be system specific, to the degree that the system definition is available at the time the assessment is being prepared, and should address projected adversary capabilities at system initial operating capability (IOC) and at IOC plus 10 years. DIA will co-chair the TSGs for ACAT ID STARs with the producing command or center. STARs for ACAT IC MDAPs and STAs for ACAT II non-MDAPs are prepared and validated by the lead service in accordance with service regulations. DIA Instruction 5000.002 describes the required STAR elements and format.
Critical Intelligence Parameters (CIPs) are established and examined through the joint and collaborative efforts of the intelligence, capability sponsor, and acquisition management community to aid in developing intelligence production requirements to support an acquisition program. CIPs are those key performance thresholds of foreign threat systems, which, if exceeded could compromise the mission effectiveness of the U.S. system in development. Adversary military doctrine, tactics, strategy, and expected employment of systems should be considered in the CIPs. Program specific CIPs, and their associated production requirements, are a key part of a STAR and will be required for validation. The inclusion of CIPs is also encouraged for STAs. If a CIP is breached, the responsible intelligence production center will notify the program office and DIA/DWO in accordance with DIA Instruction 5000.002. DIA/DWO will notify the appropriate organizations in the Office of the Secretary of Defense.
At the discretion of the responsible TSG, STARs/STAs can be used to support multiple programs which address like performance attributes, share an employment CONOPs, and have a similar employment timeline. Individual system descriptions and CIPs are still required to support the generation of the STAR.
Major Automated Information System (MAIS) programs use the Joint Information Operations Working Group and DIA-validated Information Operations (IO) Capstone Threat Assessment or service produced System Threat Assessment Report. DIA will validate service produced ACAT IAM STARs when the IO CTA is not used. Non-MAIS programs are encouraged to use the IO Capstone Threat Assessment or service produced System Threat Assessment Report as their threat baseline. MAIS programs still need to provide system descriptions, as well as the CIPs and production requirements that are specific to their program's needs.
8.1.3. Threat Validation
As noted above, for Major Defense Acquisition Programs (MDAPs) subject to Defense Acquisition Board review, the Defense Intelligence Agency (DIA) validates System Threat Assessment Reports (STARs) for Acquisition Category (ACAT) ID/ Major Defense Acquisition Programs (MDAPs). STARs for ACAT IC MDAPs and System Threat Assessments for ACAT II programs are validated by the appropriate service. DIA validation assesses the appropriateness and completeness of the intelligence, consistency with existing intelligence positions, and the use of accepted analytic tradecraft in developing the assessments. Working with its partners in the DOD intelligence community and, as needed, in the larger intelligence community, validation is intended to ensure that all relevant data is considered and appropriately used by author(s) of the assessment.
DIA validates threat information contained in Joint Capabilities Integration and Development System documents as described in the JCIDS Manual. When requested by the appropriate authority, DIA may also validate other threat information not contained in the STAR but needed for program development.
8.1.4. Support to Operational Test and Evaluation
The Test and Evaluation Master Plan should define specific intelligence requirements to support program operational test and evaluation. When requested by the appropriate authority in the offices of the Director, Operational Test and Evaluation (DOT&E) or the Under Secretary of Defense for Acquisition, Technology and Logistics (USD(AT&L)), DIA, working with the Department of Defense Intelligence Community (DoD IC), will provide additional intelligence support to the operational testing of programs on the annual DOT&E Oversight List. DIA support will not include the validation of specific testing scenarios or the validation of "Blue" (see paragraph 8.1) surrogate systems or platforms, but can include certification that the threat information in the test plan is correct and consistent with existing assessments.
Per DoD Instruction 5000.02 certain programs on the DOT&E Oversight List are to be considered as MDAPs for testing and evaluation purposes and will require a System Threat Assessment Report regardless of Acquisition Category designation.


