4.3.8. Technical Data Management Process
4.3.8. Technical Data Management Process
Through the Technical Data Management process, the program identifies, acquires, manages, maintains, and ensures access to the technical data and computer software required to manage and support a system throughout the acquisition life cycle. Key Technical Data Management considerations include understanding and protecting Government intellectual property and data rights, achieving competition goals, maximizing options for product support, and enabling performance of downstream life-cycle functions. DoDI 5000.02 contains Technical Data Management requirements for Acquisition Category (ACAT) I and II programs.
Effective acquisition, upgrades, and management of product data provide:
- Information necessary to understand and evaluate system designs throughout the life cycle
- Ability to operate and sustain weapon systems under a variety of changing technical, operational, and programmatic environments
- Ability to re-compete item acquisition, upgrades, and sustainment activities in the interest of achieving cost savings; the lack of product data and/or data rights often makes it difficult or impossible to award contracts to anyone other than the original manufacturer, thereby taking away much or all of the Government’s ability to reduce total ownership costs (TOC)
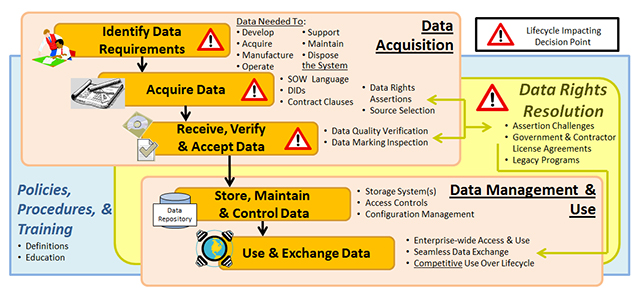
Activities and Products
The Program Manager and Systems Engineer, in conjunction with the Product Support Manager, should ensure that life-cycle requirements for weapon system-related data products and data rights are identified early and that appropriate contract provisions are put in place to enable deliveries of these products. Figure 4.3.8.F1 shows the activities associated with Technical Data Management, including:
- Identify Data Requirements
- Formulate the program’s Technical Data Rights Strategy (TDRS) and technical data management approach, with emphasis on technical and product data needed to support the product throughout its life cycle. (see DAG Chapter 2 Program Strategies for more information about Data Rights).
- Ensure that data requirements are documented in the TDRS; summarized in the Technology Development Strategy (TDS), Acquisition Strategy (AS), and Life-Cycle Sustainment Plan (LCSP); and submitted at each milestone prior to award of the contract for the next life-cycle phase.
- Consider not only the immediate, short-term costs of acquiring the needed technical data and data rights but also the long-term cost savings resulting from the ability to compete production and logistics support activities and reduce TOC. Understand that the Government can possess either Government Purpose or Unlimited Rights to use many types of technical data and data rights, at no additional cost, based on the type of technical data and the source of funding used to generate the data (see DoD Open Systems Architecture Contract Guidebook for Program Managers for more information about data rights).
- Acquire Data
- Use explicit contract Statement of Work tasks to require the developer to perform the work that generates the required data. The content, format, and quality requirements should be specified in the contract.
- Use current, approved Data Item Descriptions (DID) and Contract Data Requirements Lists (CDRL) in each contract to order the delivery of the required technical data and computer software.
- Receive, Verify, and Accept Data
- Ensure verification of content, format, and quality of all required product-related data received from originators.
- Inspect contractually ordered data deliverables to ensure markings are in accordance with the relevant data rights agreements and DFARS clauses, and contain appropriate distribution statements and/or export control statements.
Caution: Acceptance of delivered data not marked consistent with the contract can result in the Government “losing” legitimate rights to technical data and can incur significant legal liability on the Government and the individual Government employees. Regaining those rights generally requires costly and time-consuming legal actions.
- Store, Maintain, and Control Data
- Budget for and fund the maintenance and upkeep of product data throughout the life cycle.
- An Integrated Data Environment (IDE) or Product Life-cycle Management (PLM) system allows every activity involved with the program to create, store, access, manipulate, and exchange digital data.
- To the greatest extent practical, programs should use existing IDE/PLM infrastructure such as repositories operated by Commodity Commands and other organizations. (Program-unique IDEs are discouraged because the high infrastructure cost; further, multiple IDEs inhibit access, sharing, and reuse of data across programs.)
- Ensure all changes to the data are made in a timely manner and are documented in the program IDE or PLM system.
- Use and Exchange Data
Plan for and establish methods for access and reuse of product data by all personnel and organizations that perform life-cycle support activities.
Figure 4.3.8.F1. Data Management Activities
In support of the Government’s requirement for a Technical Data Package (TDP), the Program Manager should also consider all product related data (e.g., technical manuals, repair instructions, and design/analysis data) to:
- Allow logistics support activities
- Better enable sustainment engineering
- Apply, implement and manage product upgrades
Contractually deliverable data should be identified and ordered at the specific “data product” level, e.g., two-dimensional drawings, three-dimensional Computer-Aided Design (CAD) models, technical manuals, etc. Figure 4.3.8.F2 provides a notional representation of different types of product-related data.
Caution: Program Managers and Systems Engineers should be aware that terms such as “technical data,” “product data,” and “TDP” are imprecise, not equivalent, and often incorrectly used interchangeably.
Resources for establishing and conducting Technical Data Management activities include but are not limited to:
Figure 4.3.8.F2. Data Taxonomy

- Data Protection
The Program Manager is responsible for protecting system data, whether the data is stored and managed by the Government or by contractors. The DoD policy with regard to data protection, marking, and release can be found in:
Data containing information subject to restrictions are protected in accordance with the appropriate guidance, contract, or agreement. Guidance on distribution statements, restrictive markings, and restrictions on use, release, or disclosure, of data can be found in the DFARS Part 252.227-7013 and 7014, and DoDI 5230.24.
When digital data is used, the data should display applicable restriction markings, legends, and distribution statements clearly visible when the data is first opened or accessed. These safeguards not only ensure Government compliance regarding the use of data but also guarantee and safeguard contractor data delivered to the Government, and extend responsibilities of data handling and use to parties who subsequently use the data.
Section 208 of Public Law 107-347 and DoD Privacy Impact Assessment (PIA) guidance requires that PIA be conducted prior to developing or purchasing any DoD information system that collect, maintain, use, or disseminate personally identifiable information about members of the public, federal personnel, DoD contractors and, in some cases, foreign nationals. Available PIA guidance provides procedures for completing and approving PIAs. For further information, see DAG Chapter 7 Acquiring Information Technology, Including National Security Systems.
All data deliverables should include distribution statements. Processes should be established to protect all data that contain critical technology information, as well as ensure that limited distribution data, intellectual property data, or proprietary data is properly handled throughout the life cycle, whether the data are in hard-copy or digital format.


