|
About IA at NSA
Partners
Rowlett Awards
Award Recipients
Background
Nomination Procedures
Links
IA News
IA Events
Open for Registration
Closed for Registration
Scheduled
IA Guidance
Media Destruction Guidance
Security Configuration Guides
Applications
Archived Guides
Cisco Router Guides
Current Guides
Database Servers
Fact Sheets
IPv6
Operating Systems
Apple Mac Operating Systems
Linux
Microsoft Windows
Sun Solaris
Supporting Documents
Switches
VoIP and IP Telephony
Vulnerability Technical Reports
Web Server and Browser Guides
Wireless
Standards Profiles
System Level IA Guidance
TEMPEST Overview
TEMPEST Products: Level I
Certified
Confirmed Deficiencies
Suspended
Terminated
No Longer Produced
TEMPEST Products: Level II
Certified
Confirmed Deficiencies
Suspended
Terminated
No Longer Produced
TEMPEST Company POCs
Certified
Suspended
Terminated
TEMPEST Zoned Equipment
IA Academic Outreach
National Centers of Academic Excellence in IA Education
CAE/IAE Program Criteria
CAE-R Program Criteria
Colloquium
Institutions
SEAL Program
Applying
FAQs
IA Courseware Evaluation Program
Institutions
FAQs
Student Opportunities
IA Business and Research
IA Business Affairs Office
Certified Product Sales and Support
Commercial COMSEC Evaluation Program
Commercial Satellite Protection Program
Independent Research and Development Program
User Partnership Program
National IA Research Laboratory
Partnerships with Industry
NIAP and COTS Product Evaluations
IA Programs
Global Information Grid
High Assurance Platform
Releases
Computing Platform Architecture and Security Criteria
IA Training and Rating Program
Inline Media Encryptor
Suite B Cryptography
IA Careers
Contact Information
|
Computing Platform Architecture and Security Criteria - NSA/CSSThe Computing Platform Architecture and Security Criteria (CPC) are the documents that formally define the computing platform architecture, the platform components, and the computing platform instances. The CPC is the basis against which product developers can demonstrate component-level or component set-level compliance of their products, and system integrators can demonstrate platform-level compliance of the platforms they integrate. The CPC has 3 sections (see Figure 1):
CPC Target Audiences
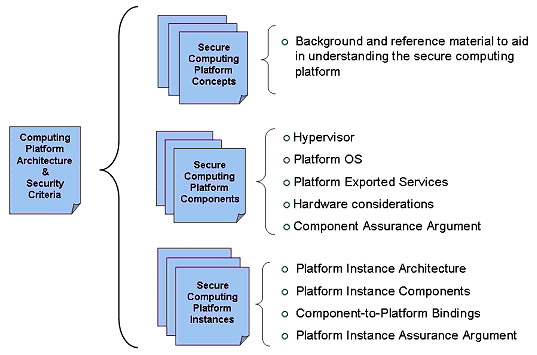 Figure 1 - Computing Platform Architecture and Security Criteria The HAP Program leads the effort to develop the CPC and takes responsibility for addressing security concerns related to all aspects of the platform definition. The HAP Program will collaborate with subject matter experts from industry, academia and the operational user community to aid in the CPC development and will rely on these subject matter experts to address all other concerns presented in defining the platform. The CPC is expected to leverage current and past efforts related to computing platform technologies and security. Figure 2 depicts some of the CPC influences.
Figure 2 - CPC Influences |
|
|
Date Posted: Jan 15, 2009 | Last Modified: Jan 15, 2009 | Last Reviewed: Jan 15, 2009 |
Top NSA Banner














