- Training
- Training Live Events
- Training Without Travel
- SANS Courses
- Certified Instructors
- Career Roadmap
- Training Calendars
- SANS @Home
- SANS OnDemand
- Community SANS
- SANS Mentor Program
- SANS Onsite
- SANS SelfStudy
- SANS Summit Series
- SANS Partnership Series
- Webcasts
- Work Study
- Events Archive
- DoD 8570
- Voucher Credit Program
- group discounts
- Certification
- Resources
- List of Resources
- Top 20 List
- Top 25 Programming Errors
- Application Security Procurement Language
- Top 10 Security Trends
- Top 5 Essential Log Reports
- Reading Room
- Webcasts
- WhatWorks
- Newsletters
- RSS Feeds
- Calendar Feeds
- Projects
- Security Policy Project
- Security+ Study Guide
- Awards & Recognitions
- SANS Buyers Guide
- Security Tool Demos
- Vendor
- Portal
- Storm Center
- College
- Developer
- About
the most trusted source for computer security training, certification and research
SANS Top-20 2007 Security Risks (2007 Annual Update)
For a continuous update on the SANS Top 20 vulnerabilities, subscribe to @Risk. If you would like the Executive Summary pointing out newsworthy highlights of the SANS 2007 Top Internet Security Risks, click here.
Client-side Vulnerabilities in:
C1. Web BrowsersC2. Office Software
C3. Email Clients
C4. Media Players
Server-side Vulnerabilities in:
S1. Web ApplicationsS2. Windows Services
S3. Unix and Mac OS Services
S4. Backup Software
S5. Anti-virus Software
S6. Management Servers
S7. Database Software
Security Policy and Personnel:
H1. Excessive User Rights and Unauthorized DevicesH2. Phishing/Spear Phishing
H3. Unencrypted Laptops and Removable Media
Application Abuse:
A1. Instant MessagingA2. Peer-to-Peer Programs
Network Devices:
N1. VoIP Servers and PhonesZero Day Attacks:
Z1. Zero Day AttacksExecutive Summary
Seven years ago, the SANS Institute and the National Infrastructure Protection Center (NIPC) at the FBI released a document summarizing the Ten Most Critical Internet Security Vulnerabilities. Thousands of organizations relied on that list, and on the expanded Top-20 lists that followed in succeeding years, to prioritize their efforts so they could close the most dangerous holes first.
The threat landscape is very dynamic, which in turn makes it necessary to adopt newer security measures. Just over the last year, the kinds of vulnerabilities that are being exploited are very different from the ones being exploited in the past. Here are some observations:
- Operating systems have fewer vulnerabilities that can lead to massive Internet worms. For instance, during 2002-2005, Microsoft Windows worms like Blaster, Nachi, Sasser and Zotob infected a large number of systems on the Internet. There have not been any new large-scale worms targeting Windows services since 2005. On the other hand, vulnerabilities found anti-virus, backup or other application software, can result in worms. Most notable was the worm exploiting the Symantec anti-virus buffer overflow flaw last year.
- We have seen significant growth in the number of client-side vulnerabilities, including vulnerabilities in browsers, in office software, in media players and in other desktop applications. These vulnerabilities are being discovered on multiple operating systems and are being massively exploited in the wild, often to drive recruitment for botnets.
- Users who are allowed by their employers to browse the Internet have become a source of major security risk for their organizations. A few years back securing servers and services was seen as the primary task for securing an organization. Today it is equally important, perhaps even more important, to prevent users having their computers compromised via malicious web pages or other client-targeting attacks.
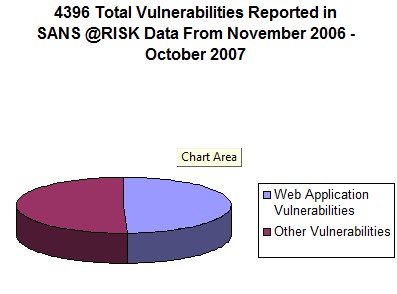
- Web application vulnerabilities in open-source as well as custom-built applications account for almost half the total number of vulnerabilities being discovered in the past year. These vulnerabilities are being exploited widely to convert trusted web sites into malicious servers serving client-side exploits and phishing scams.
- The default configurations for many operating systems and services continue to be weak and continue to include default passwords. As a result, many systems have been compromised via dictionary and brute-force password guessing attacks in 2007!
- Attackers are finding more creative ways to obtain sensitive data from organizations. Therefore, it is now critical to check the nature of any data leaving an organization's boundary.
The SANS Top 2007 is a consensus list of vulnerabilities that require immediate remediation. It is the result of a process that brought together dozens of leading security experts. They come from the most security-conscious government agencies in the UK, US, and Singapore; the leading security software vendors and consulting firms; the top university-based security programs; the Internet Storm Center, and many other user organizations. A list of participants appears at the end of this document.
The SANS Top 2007 list is not "cumulative." We include only critical vulnerabilities from the past year or so. If you have not patched your systems for long time, it would be wise to patch the vulnerabilities listed in the Top 20 2006 list as well as those in the prior lists. At the end of this document, you will find a short FAQ (list of frequently asked questions) that answers questions you may have about the project and the way the list is created.
This year's list of top risks diverges from lists in past years that focused on very specific technical vulnerabilities that could be fixed by tweaking a configuration or applying one patch. Because attackers are moving so quickly today, such point-fixes are outdated almost immediately. For that reason, this year's list of top risks focuses more on the areas that attackers are targeting and where organizations need to enhance their security processes to ensure consistent application of technical fixes.
The SANS Top 2007 is a living document. It includes step-by-step instructions and pointers to additional information useful for correcting the security flaws. We will update the list and the instructions as more critical threats and more current or convenient methods of protection are identified, and we welcome your input along the way. This is a community consensus document -- your experience in fighting attackers and in eliminating the vulnerabilities can help others who come after you. Please send suggestions via e-mail to top20@sans.org
Version 8.0 November 28, 2007
Copyright © 2007, SANS Institute
Questions / comments may be directed to top20@sans.org.
To link to the Top 20 List, use the "SANS Top 20 List" logo
PDF Version |
Printer Friendly Version
- Want to receive updates to the Top20 list?
- Subscribe to the Top20 mailing list at:
http://lists.sans.org/mailman/listinfo/top20-announce - Related Resources
- SANS Top 20 FAQ
- Press Release (2007-11-28)
- Free Testing Tools
- Qualys:
https://sans20.qualys.com - Applicure Technologies:
www.applicure.com/?page=Sans - Tenable Security:
http://blog.tenablesecurity.com/ - Top 20 In The News
- Please check back
- Top 20 Archive
- November, 2007 - Version 8 (Current)
- November, 2006 - Version 7
- November, 2005 - Version 6
- October, 2004 - Version 5
- October, 2003 - Version 4
- October, 2002 - Version 3
- May, 2001 - Version 2
- June, 2000 - Version 1 (Original Top 10)
- Top 20 List v8 Update Log
- 2007-11-28 - v8.0: Inital Release
- Top 20 Translations
- Contact top20@sans.org to collaborate in the translation of the Top 20 to your own language.
- Korean - v.8.0 - Added January 24, 2008
- Japanese - v.8.0 - Added May 21, 2008
- NOTE: These translations are a volunteer effort. Our deep gratitude to the individuals and organizations that invested their time and work to help the community.
Client-side Vulnerabilities in:
C1. Web Browsers
C1.1 Description
Microsoft Internet Explorer is the world's most popular web browser and is installed by default on every Microsoft Windows system. Unpatched or older versions of Internet Explorer contain multiple vulnerabilities that can lead to memory corruption, spoofing and execution of arbitrary scripts or code. The most critical issues are the ones that lead to remote code execution without any user interaction when a user visits a malicious web page or reads a malicious email. Exploit code for many of these critical Internet Explorer flaws is publicly available. In addition, Internet Explorer has been leveraged to exploit vulnerabilities in other core Windows components such as HTML Help and the Graphics Rendering Engine. During the past year, hundreds of vulnerabilities in ActiveX controls installed by Microsoft and other software vendors have been discovered. These are also being exploited via Internet Explorer.
Mozilla Firefox is the second most popular web browser after Internet Explorer. It also has a fair share of vulnerabilities. In 2007, it has released several updates to address publicly disclosed vulnerabilities. Similarly to Internet Explorer, unpatched or older versions of Firefox contain multiple vulnerabilities that can lead to memory corruption, spoofing and execution of arbitrary scripts or code. The web sites exploiting the browser vulnerabilities typically host a several exploits, and even launch the appropriate exploit(s) based on which browser the potential victim is using.
With the explosion of rich content in web sites, a parallel increase has been seen in the number of Browser Helper Object and third-party plug-ins used to access various MIME file types such as multimedia and documents. These plug-ins often support client-side web scripting languages such as Macromedia Flash or Shockwave. Many of these plug-ins are installed (semi-)transparently by a website. Users may thus not be aware that an at-risk helper object or plug-in is installed on his/her system. These additional plug-ins introduce more avenues for hackers to exploit to compromise computers of users visiting malicious web sites.
In October 2007, for example, systems running Windows XP and Windows Server 2003 with Windows Internet Explorer 7 were found not to handle specially crafted Uniform Resource Identifiers (URIs) properly. By creating a specially crafted URI in a PDF document attackers were able to execute arbitrary commands on vulnerable systems.
While some plug-ins such as Adobe Reader and Quicktime perform version checks and provide an update feature, these are often bothersome and ignored by users. It is often also difficult to detect which version of a plug-in is installed. For example, systems may have different versions of Shockwave installed for reasons of backward compatibility, but the user cannot easily discover which version or versions are running.
These flaws have been widely exploited to install spyware, adware and other malware on users' systems. The spoofing flaws have been leveraged to conduct phishing attacks. In some cases, these vulnerabilities were zero-days i.e. no patch was available at the time the vulnerabilities were publicly disclosed. Many reported plug-ins were also widely exploited by malicious web sites before patches were made available by the vendor.
In 2007 alone, Microsoft has released multiple updates for Internet Explorer.
- Cumulative Security Update for Internet Explorer (939653) (MS07-057)
- Vulnerability in Vector Markup Language Could Allow Remote Code Execution (938127) (MS07-050)
- Cumulative Security Update for Internet Explorer (937143) (MS07-045)
- Cumulative Security Update for Internet Explorer (933566) (MS07-033)
- Vulnerabilities in GDI Could Allow Remote Code Execution (925902) (MS07-017)
- Cumulative Security Update for Internet Explorer (931768) (MS07-027)
- Cumulative Security Update for Internet Explorer (928090) (MS07-016)
- Vulnerability in Vector Markup Language Could Allow Remote Code Execution (929969) (MS07-004)
Note that the latest cumulative update for Internet Explorer includes all the previous cumulative updates. Also note that MS07-017 does not list vulnerabilities in Internet Explorer; however, the most common avenue of exploitation is via Internet Explorer.
C1.2 Operating Systems Affected
While in theory any web browser on any operating system is vulnerable, the most common web browsers will tend to be targeted most by attackers. The two most popular web browsers on the Internet today are Microsoft Internet Explorer and Mozilla Firefox.
Internet Explorer 5.x, 6.x and 7 running on all versions of Windows are affected
Firefox running on any version of compatible operating systems is potentially vulnerable.
As plug-ins are generally used to enable access to third party file formats, many plug-in vulnerabilities apply to all compatible browsers on all operating systems. Any web browser running on any version of any operating system is potentially vulnerable.
C1.3 CVE Entries
Internet Explorer
CVE-2006-4697,
CVE-2007-0024,
CVE-2007-0217,
CVE-2007-0218,
CVE-2007-0219,
CVE-2007-0942,
CVE-2007-0944,
CVE-2007-0945,
CVE-2007-0946,
CVE-2007-0947,
CVE-2007-1749,
CVE-2007-1750,
CVE-2007-1751,
CVE-2007-2216,
CVE-2007-2221,
CVE-2007-2222,
CVE-2007-3027,
CVE-2007-3041,
CVE-2007-3826,
CVE-2007-3892,
CVE-2007-3896
Firefox
CVE-2007-0776,
CVE-2007-0777,
CVE-2007-0779,
CVE-2007-0981,
CVE-2007-1092,
CVE-2007-2292,
CVE-2007-2867,
CVE-2007-3734,
CVE-2007-3735,
CVE-2007-3737,
CVE-2007-3738,
CVE-2007-3845,
CVE-2007-4841,
CVE-2007-5338
Adobe Acrobat Reader
CVE-2007-0044,
CVE-2007-0046,
CVE-2007-0103,
CVE-2007-5020
The CVEs for plug-ins like Media Players are listed in the section C4.
C1.4 How to Determine If You Are at Risk
You can use any vulnerability scanner to check whether your systems are patched against these vulnerabilities.
For Internet Explorer, consider using the Microsoft Windows Server Update Services (WSUS), Microsoft Baseline Security Analyzer (MBSA), Windows Live Scanner or Systems Management Server (SMS) to check the security patch status of your systems.
To see the plug-ins most recently used by Internet Explorer 7, select Tools -> Internet Options. Under the Programs tab, select Manage Add-ons. You can select different views of browser plug-ins, including those currently loaded, plug-ins that have been used by Internet Explorer, and those configured to run without requiring permission. You can disable any of these by clicking on a specific add-on and selecting Disable.
For Firefox, select Tools -> Options -> Content -> File Types -> Manage to see how Firefox will handle various file formats.
Third-parties have begun releasing tools, such as Secunia PSI (currently in beta), which scan for browser helper object versions and patches.
C1.5 How to Protect against These Vulnerabilities
- If you are using Internet Explorer on your Windows XP system, the best way to remain secure is to upgrade to Windows XP Service Pack 2. The improved operating system security and Windows Firewall will help mitigate risk. For those unable to use Windows XP with Service Pack 2, switching away from Internet Explorer to an alternative browser is the safest path.
- Users should upgrade to version 7 of Internet Explorer, which provides improved security over previous versions. The latest version of Internet Explorer, IE7, is being distributed by Microsoft as a Critical Update (KB926874)
- Keep the systems updated with all the latest patches and service packs. If possible enable Automatic Updates on all systems.
- Pay attention to Microsoft Security Advisories; implementing suggested mitigations before the patch becomes available could alleviate exposure to zero day attacks.
- To prevent exploitation of remote code execution vulnerabilities at Administrator level, use tools like Microsoft DropMyRights to implement "least privileges" for Internet Explorer.
- Prevent vulnerable ActiveX components from running inside Internet Explorer via the "killbit" mechanism.
- Many spyware programs are installed as Browser Helper Objects. A Browser Helper Object or BHO is a small program that runs automatically every time Internet Explorer starts and extends the browser's capabilities. Browser Helper Objects can be detected with Antispyware scanners.
- Use intrusion prevention/detection systems, anti-virus, anti-spyware and malware detection software to block malicious HTML script code.
- Windows 98/ME/NT are no longer supported for updates. Legacy users should consider upgrading to Windows XP.
- Consider using other browsers such as Mozilla Firefox that do not support ActiveX technology.
C1.6 How to Secure Web Browsers
To configure the security settings for Internet Explorer:
- Select Internet Options under the Tools menu.
- Select the Security tab and then click Custom Level for the Internet zone.
- Most of the flaws in IE are exploited through Active Scripting or ActiveX Controls.
- Under Scripting, select Disable for Allow paste operations via script to prevent content from being exposed from your clipboard. Note: Disabling Active Scripting may cause some web sites not to work properly. ActiveX Controls are not as popular but are potentially more dangerous as they allow greater access to the system.
- Select Disable for Download signed and unsigned ActiveX Controls. Also select Disable for Initialize and script ActiveX Controls not marked as safe.
- Java applets typically have more capabilities than scripts. Under Microsoft VM, select High safety for Java permissions in order to properly sandbox the Java applet and prevent privileged access to your system.
- Under Miscellaneous select Disable for Access to data sources across domains to avoid cross-site scripting attacks.
- Ensure that no un-trusted sites are in the Trusted sites or Local intranet zones as these zones have weaker security settings than the other zones.
- Microsoft has published a "Internet Explorer 7 Desktop Security Guide" to enhance Internet Explorer security. It examines the new features and setting that can be modified to provide a more "locked down" security configuration for Internet Explorer 7.
To configure the security settings for Firefox:
- Select Options under the Tools menu.
- Further customization of Firefox configuration can be obtained at http://kb.mozillazine.org/About:config.
To update the plug-ins used by the web browsers:
- Most plug-ins come with "Check for Updates" feature. It can usually be found under "Options", Preferences" or "Help" menus.
- Select the "Check for Updates" to ensure you have the latest version of the software.
C1.7 References
US-CERT Securing Web Browser Information
http://www.us-cert.gov/reading_room/securing_browser/browser_security.html
Internet Explorer 7 Desktop Security Guide
http://www.microsoft.com/downloads/details.aspx?FamilyID=6AA4C1DA-6021-468E-A8CF-AF4AFE4C84B2&displaylang=en
Microsoft Internet Explorer Weblog
http://blogs.msdn.com/ie/
Mozilla Security Center
http://www.mozilla.org/security/
Firefox Vulnerabilities
http://www.mozilla.org/projects/security/known-vulnerabilities.html
@Risk: The Consensus Security Alert
https://www.sans.org/newsletters/risk/
C2. Office Software
C2.1 Description
This section includes vulnerabilities for office productivity suites that include e-mail clients, word processors, spreadsheet applications, document viewers and presentation applications. Vulnerabilities in office products are typically exploited via the following attack vectors:
- An attacker sends a specially crafted office document in an email. When the attachment is opened, the malformed contents in the document exploit vulnerabilities in the office software.
- An attacker hosts a malicious document on a web server or shared folder, and entices a user to browse to the web page or the shared folder. Note that, in most situations, Internet Explorer automatically opens Microsoft Office documents. Hence, browsing the malicious web page or folder is sufficient for vulnerability exploitation in many cases.
- An attacker runs an NNTP (news) server or hijacks an RSS feed that sends malicious documents to news and RSS clients.
In all these scenarios, viruses, trojans, spyware, ad-ware, rootkits, keyboard loggers, or any other program of the attacker's choice, can be installed on victim's computer.
Microsoft Office is the most widely used email and productivity suite worldwide. It includes Outlook, Word, PowerPoint, Excel, Visio, FrontPage and Access. A large number of critical flaws were reported in MS Office applications and a few of them (CVE-2006-5574, CVE-2006-1305, CVE-2006-6456, CVE-2006-6561, CVE-2006-5994, CVE-2007-0515, CVE-2007-0671, CVE-2007-0045) were zero-day issues in which exploit code, technical details or proof-of-concept was publicly disclosed before any fix became available from Microsoft.
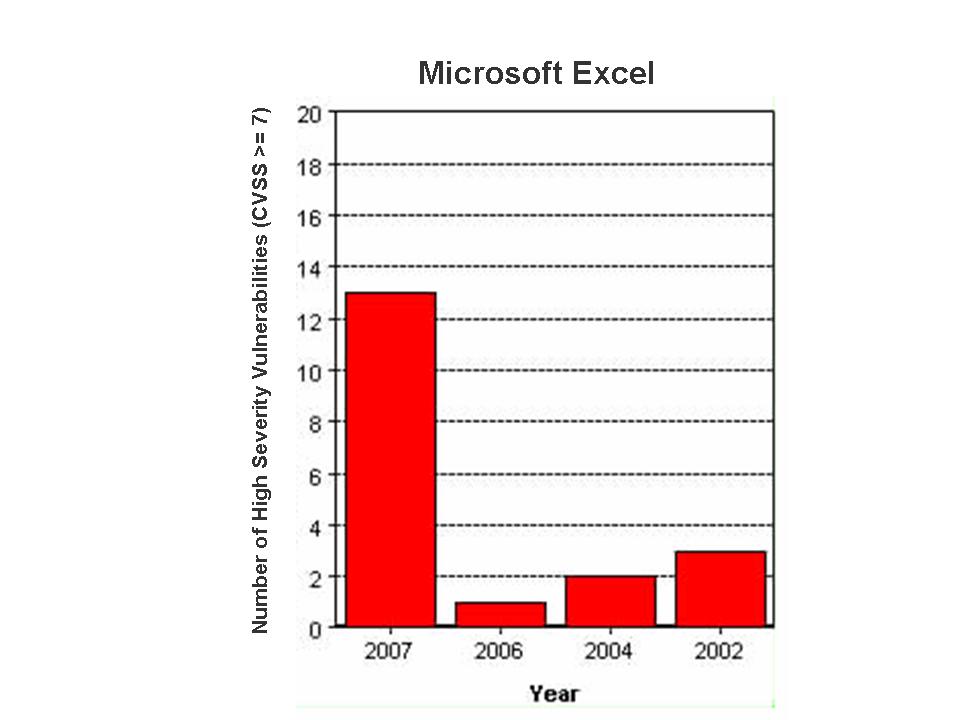
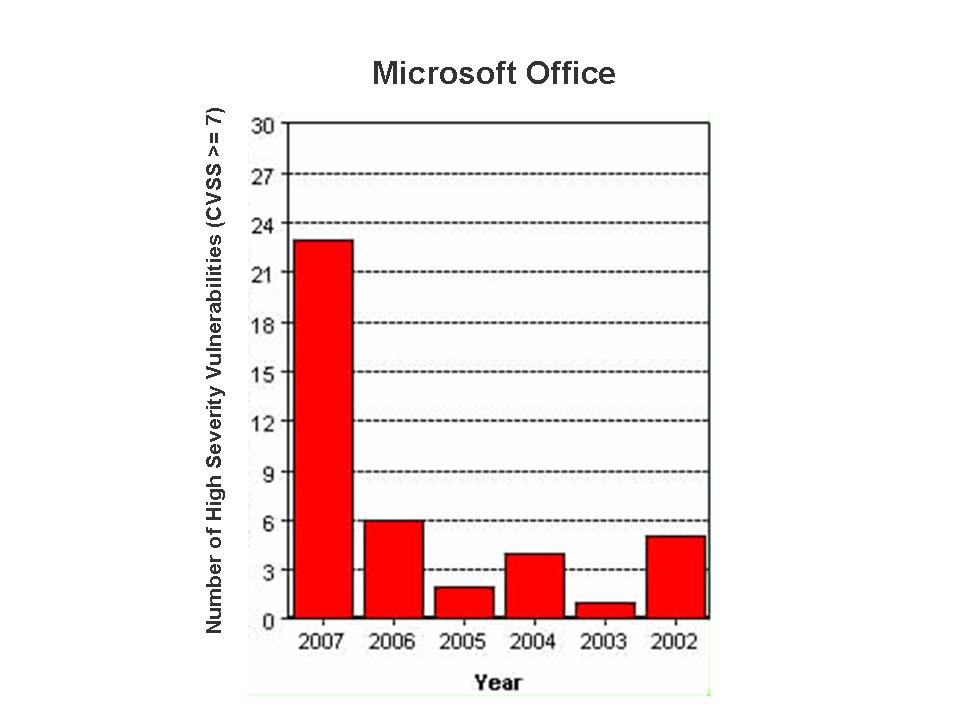
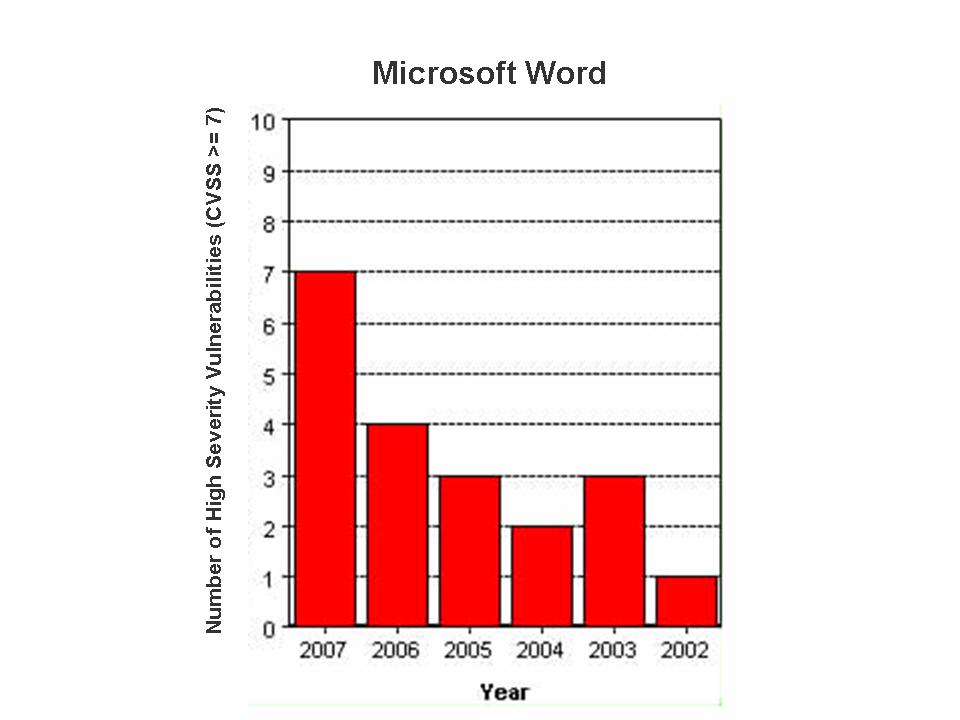
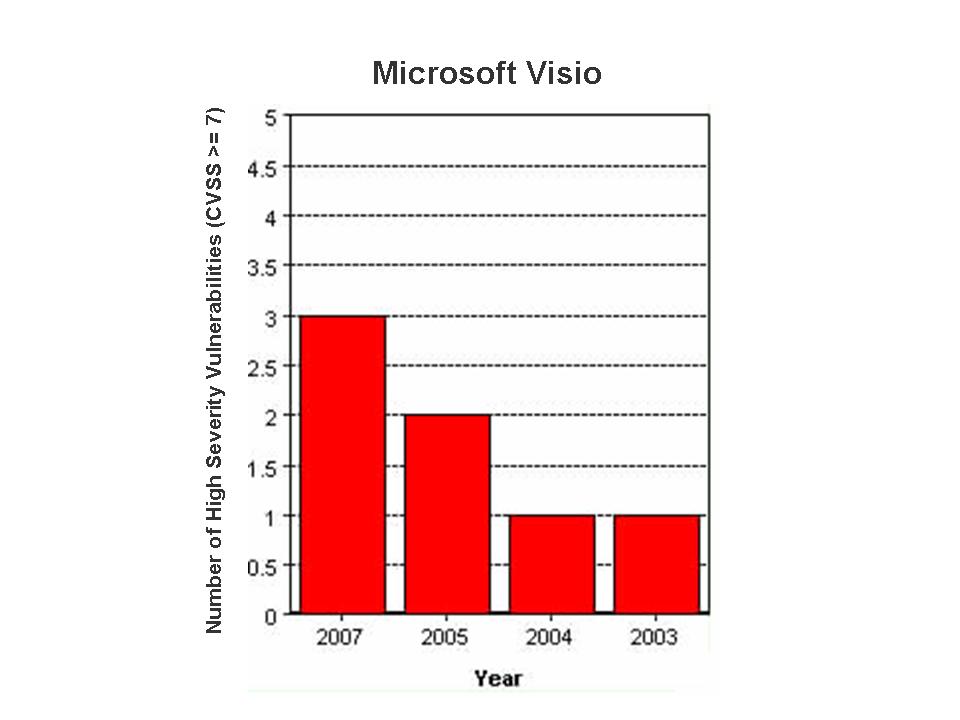
The critical flaws that were reported this year in Office products:
- Microsoft Excel Remote Code Execution (MS07-002)
- Microsoft Outlook Remote Code Execution (MS07-003)
- Microsoft Word Remote Code Execution (MS07-014)
- Microsoft Office Remote Code Execution (MS07-015)
- Microsoft Excel Remote Code Execution (MS07-023)
- Microsoft Word Remote Code Execution (MS07-024)
- Microsoft Office Remote Code Execution (MS07-025)
- Microsoft Outlook Express and Windows Mail (MS07-034)
- Microsoft Excel Remote Code Execution (MS07-036)
- Microsoft Excel Remote Code Execution (MS07-044)
- Adobe Reader and Acrobat Remote Code Execution (APSB07-18)
- Adobe Reader and Acrobat Cross Site Scripting (APSA07-01)
C2.2 Operating Systems Affected
Windows 9x, Windows 2000, Windows XP, Windows 2003, Windows Vista,
MacOS X are all
vulnerable depending on the version of Office software installed.
C2.3 CVE Entries
CVE-2007-0027,
CVE-2007-0028,
CVE-2007-0029,
CVE-2007-0030,
CVE-2007-0031,
CVE-2007-0034,
CVE-2007-0208,
CVE-2007-0209,
CVE-2007-0515,
CVE-2007-0671,
CVE-2007-0215,
CVE-2007-1203,
CVE-2007-0035,
CVE-2007-0870,
CVE-2007-1747,
CVE-2007-1658,
CVE-2007-1756,
CVE-2007-3030,
CVE-2007-3890
C2.4 How to Determine If You Are at Risk
Microsoft Office installations running without the patches referenced in the Microsoft Bulletins listed from the CVE entries are vulnerable. Use a vulnerability scanner to check whether your systems are patched against these vulnerabilities. Also consider using the Microsoft Windows Server Update Services (WSUS), Microsoft Baseline Security Analyzer (MBSA), Windows Live OneCare or Systems Management Server (SMS) to check the security patch status of your systems.
C2.5 How to Protect against Office Vulnerabilities
- Keep the systems updated with all the latest patches and service packs. If possible enable Automatic Updates on windows systems.
- Do not open attachments from unknown sources. Practice caution when opening unexpected e-mail attachments even from known sources.
- Do not “click browse” to avoid opening documents from unknown web sites. Click browsing is a habit of browsing the web by clicking on links in e-mails or online forums. Use the bookmark feature in every browser to create links to your frequently used web sites.
- Disable the Internet Explorer feature of automatically opening Office documents.
- Configure Outlook and Outlook Express with enhanced security.
- Use a vulnerability scanner to determine your risk.
- Use intrusion prevention/detection systems and anti-virus and malware detection software to prevent malicious server responses and documents from reaching end users.
- Use mail and web filtering systems at the network perimeter to prevent malicious Office documents from reaching end-user systems.
C2.6 References
Securing Microsoft Office
http://www.microsoft.com/technet/security/guidance/clientsecurity/2007office/default.mspx
C3. Email Clients
C3.1 Description
E-mail is one of the vital applications of the Internet. E-mail provides tremendous savings it terms of time, money and efficiency. Given its omnipresence, e-mail provides a common vector for multiple vulnerabilities.
Multiple avenues of attack that can be employed through email:
- Distribution of malware (viruses, Trojans, keyloggers, spyware, adware, rootkits etc);
- Phishing - Attempts to lure email user into revealing his/her passwords or other confidential information;
- Spam - unsolicited (junk) email;
- Social engineering;
- Denial of service attacks - sending high volume of email messages to a potential “victim” server or mailbox;
These attacks can result in:
- damage to applications, data, or operating system;
- disclosure of confidential information;
- propagation of malware;
- use of affected systems as “bots” (infected machines under the control of persons other than the intended users, used as proxies for attacks on other systems or for storage and distribution of pirated content and pornography);
- lack of availability of systems and services;
- waste of time, money and labor.
Virtually all contemporary operating systems can be used as platforms for e-mail client applications.
The most popular e-mail applications currently are
- Microsoft Outlook (Microsoft Windows only) and Outlook Express (Microsoft Windows only; old versions were available for Apple Macintosh);
- Mozilla Thunderbird (Microsoft Windows, Linux, Mac OS X);
- Mail.app (Macintosh only)
There are other popular email clients (Opera mail, Pegasus, Mozilla SeaMonkey, The Bat!, Eudora etc), but their usage share is relatively low.
No matter what operating system or e-mail client application is used, precautions should be taken whenever handling email (See C3.4 How to Protect Against The Email Vulnerabilities for details).
C3.2 Operating Systems Affected
Windows 2000 Workstation and Server, Windows XP Home and Professional, Windows Vista, Windows Server 2003, Mac OS X, Linux and Unix are all potentially vulnerable.
C3.3 CVE Entries
Microsoft Outlook Express, Outlook, Vista Windows Mail
CVE-2006-4868,
CVE-2007-0033,
CVE-2007-0034,
CVE-2007-3897
Mozilla Thunderbird, SeaMonkey
CVE-2006-4565,
CVE-2006-4571,
CVE-2006-5463,
CVE-2006-5747,
CVE-2006-6502,
CVE-2006-6504,
CVE-2007-0777,
CVE-2007-0779,
CVE-2007-1282,
CVE-2007-2867,
CVE-2007-3734,
CVE-2007-3735,
CVE-2007-3845
Eudora
CVE-2006-0637,
CVE-2006-6024,
CVE-2006-6336,
CVE-2007-2770
C3.4 How To Protect Against Vulnerabilities in Email Clients
- Remove all e-mail client software from production server systems, or where otherwise unnecessary.
- Do not to run any email client on servers or workstations with confidential information.
- When you must run any email client application on any system, be sure to:
- Use the latest version of the email client and enable the automatic update feature provided by the application or operating system.
- Use anti-virus software with current virus signatures. Configure the anti-virus software to monitor files in real-time if possible, and configure automatic daily update of virus signatures if possible.
- Do not run the email client as an administrative user, or other user account with elevated privileges.
- If you absolutely must run email while logged on as Administrator on Windows system, use tools like “Drop My Rights” for lowering privileges available to the email application.
- Do not open any email messages from unknown or suspicious sender;
- Do not answer junk mail (spam), even if there is an option to unsubscribe;
- View email messages as plain text, or with as little formatting as possible: HTML and RTF (two common enhanced formatting schemes for email messages) can allow scripting and other avenues for exploitation;
- Do not open any attachments without scanning them first with anti-virus program;
- Configure your email client to not send return receipts or read confirmations;
- For secure email exchange use digital signatures or/and encryption.
Application-specific configuration details and, settings that can improve security of email client
Outlook/Outlook Express/Windows Mail
Outlook Express is bundled with Internet Explorer and installed by default on Windows 98, 2000, XP, 2003.
Windows Vista replaced Outlook Express with Windows Mail.
- If Outlook Express is not required on the system, it is recommended to uninstall it.
- If Outlook Express is installed on the system, keep it updated.
- Outlook Express updates are bundled with Internet Explorer updates, so updating Internet Explorer to the new version or service pack level also upgrades Outlook Express.
Configuration settings for Outlook Express
- Outlook Express - Tools - Options - Read - Select “Read all messages in plain text”
- Outlook Express - Tools - Options - Receipts - Select “Never send a read receipt”
- Outlook Express - Tools - Options - Security - Select the Internet Explorer security zone to use - Select “Restricted sites zone”
- Outlook Express - Tools - Options - Security - Select “Warn me when other applications try to send mail as me”
- Outlook Express - Tools - Options - Security - Select “Do not allow attachments to be saved or opened that could potentially be a virus”
- Outlook Express - Tools - Options - Security - Select “Block images and other external content in HTML email”
- Outlook Express - Tools - Options - Maintenance - Select “Empty messages from the Deleted Items folder on exit”
- Outlook Express - Tools - Accounts - Mail - Select “Properties” for each email account - Server - Unselect “Remember password”
Configuration settings for Outlook
Settings for Outlook 2003:
- Outlook - Tools - Options - Preferences - Email Options - Select “Read all standard mail in plain text”
- Outlook - Tools - Options - Security - Security Zones - Zone - Select “Restricted sites”
- Outlook - Tools - Options - Security - Download pictures - Change Automatic Download settings - Select “Don’t allow pictures or other content automatically in HTML e-mail”
- Outlook - Tools - Options - Security - Download pictures - Change Automatic Download settings - Select “Warn me before downloading content when editing, forwarding or replying to e-mail”
- Outlook - Tools - Options - Preferences - Junk e-mail - Options - Choose the level of junk e-mail protection you want - Select “Low”, “High” or “Safe Lists only”
- Outlook - Tools - Options - Preferences - Junk e-mail - Options - Select “Don’t turn on links in messages that might connect to unsafe or fraudulent sites”
- Outlook - Tools - Options - Other - Select “Empty the Deleted Items folder upon exiting”
- Outlook - Tools - E-mail Accounts - Select “Change…” for each email account - Unselect “Remember password”
Same or similar settings can be accessed in Outlook 2007 as follows:
Outlook 2007 - Tools - Trust Center - E-mail Security
Configuration settings for Mozilla Thunderbird (versions 2.0 and later)
- Thunderbird - View - Message body as - Select “Plain text”
- Thunderbird - View - Unselect “Display attachments inline”
- Thunderbird - Tools - Options - Advanced - Config editor … - javascript.allow.mailnews - Set to “False”
- Thunderbird - Tools - Options - Advanced - Config editor … - javascript.enabled - Set to “False”
- Thunderbird - Tools - Options - Advanced - Config editor … - javascript.options.strict - Set to “True”
- Thunderbird - Tools - Options - Privacy - E-mail scams - Select “Tell me if the message I’m reading is a suspected email scam”
- Thunderbird - Tools - Options - Privacy - Anti-Virus - Select “Allow anti-virus clients to quarantine individual messages”
C3.5 References
Browsing the Web and Reading E-mail Safely as an Administrator
http://msdn2.microsoft.com/en-us/library/ms972827.aspx
How to view all e-mail messages in plain text format
http://support.microsoft.com/kb/831607
Overview of Cryptography in Outlook 2003
http://office.microsoft.com/en-us/ork2003/HA011402871033.aspx
Digital signatures and encryption (Outlook 2007)
http://office.microsoft.com/en-us/outlook/CH100622261033.aspx
Service Packs (Microsoft Office and Microsoft Outlook)
http://support.microsoft.com/sp/
Microsoft Office downloads
http://office.microsoft.com/en-us/downloads/FX101321101033.aspx?pid=CL100570421033
Block or unblock links in suspicious phishing messages
http://office.microsoft.com/en-us/outlook/HA011841931033.aspx
Customizing the Outlook Security Features Administrative Package
http://office.microsoft.com/en-us/orkXP/HA011364471033.aspx
Security and privacy-related preferences (Thunderbird)
http://kb.mozillazine.org/Category:Security_and_privacy-related_preferences
Security Policies (Thunderbird)
http://kb.mozillazine.org/Security_Policies
C4. Media Players
C4.1 Description
To play or display any multimedia content (music, video, pictures, drawings, etc.), regardless of origin, your computer needs an application called a media player. Music and videos are commonly downloaded from the Internet, usually for entertainment, news, education, and/or business content.
Most modern operating systems are automatically configured with at least one standard media player software package. Third party applications are also available that play formats not normally supported by the standard application set. Such support is usually required for proprietary formats that vendors must license in order to add compatibility to their media player application. These additional applications are usually installed on an as-needed basis - at times even automatically - in order to provide support for the requested multimedia content. Once these applications are installed they may be easily forgotten and overlooked by IT administrators who are responsible for patch management and support, usually because they are not aware of their existence on each deployed system.
Over the past year vulnerabilities have been released for most popular media players available today. While the severity of the vulnerabilities varies, these vulnerabilities can often be used to install malware such as viruses, bot-net applications, root kits, spy-ware, and ad-ware.
While this list does provide a detailed overview of popular media players and their associated vulnerabilities, it does not attempt to be an exhaustive list of all media players and their associated vulnerabilities. Many of these vulnerabilities do have publicly available exploit code and are being actively exploited in the wild.
The media players for the major platforms are:
- Windows: Windows Media Player, RealPlayer, Apple Quicktime, Adobe Flash Player, Apple iTunes
- Mac OS: RealPlayer, Apple Quicktime, Apple iTunes, Adobe Flash Player
- Linux/Unix: RealPlayer, Adobe Flash Player
C4.2 Operating Systems Affected
- Microsoft Windows
- Linux/Unix
- Mac OS X
C4.3 CVE Entries
RealPlayer
CVE-2007-2497,
CVE-2007-3410,
CVE-2007-5601
Apple iTunes
CVE-2007-3752
Adobe Flash Player
CVE-2007-3457,
CVE-2007-5476
Apple Quicktime
CVE-2007-0462,
CVE-2007-0588,
CVE-2007-0466,
CVE-2007-0711,
CVE-2007-0712,
CVE-2007-0714,
CVE-2007-2175,
CVE-2007-2295,
CVE-2007-2296,
CVE-2007-0754,
CVE-2007-2388,
CVE-2007-2389,
CVE-2007-2392,
CVE-2007-2393,
CVE-2007-2394,
CVE-2007-2396,
CVE-2007-2397,
CVE-2007-5045,
CVE-2007-4673
Windows Media Player
CVE-2006-6134,
CVE-2007-3035,
CVE-2007-3037,
CVE-2007-5095
C4.4 How to Determine If You Are Vulnerable
Using any media player that has not been patched or upgraded to the most recent version is a potential problem. Good system inventory and patch management practices will help you be proactive against threats from and attacks via media player applications.
C4.5 How to Protect Against Media Player Vulnerabilities
The following are some common best practices to protect against vulnerabilities associated with media players:
- Ensure media players are regularly updated with all the latest patches. Most players support updating via the help or tools menus.
- Carefully review default installations of operating systems and other products to ensure they do not include unwanted media players.
- Configure operating systems and browsers to prevent unintentional installation.
- Use anti-malware tools such as anti-virus and IDS software on the client desktop to prevent compromise.
- On centrally managed systems use the principle of least privilege, and limit installation of additional software by the end-user, when possible. This will make patch management and vulnerability management easier and more affective.
- On centrally managed systems when possible inventory installed software in order to identify potential risks in the environment.
- Install media player components only on systems requiring such components (e.g. workstations vs. servers).
C4.6 References
RealNetworks Media Player Products Home Page
http://www.realnetworks.com/products/media_players.html
http://www.realnetworks.com/support/updates.html
Apple QuickTime Home Page
http://www.apple.com/quicktime/
http://www.apple.com/support/quicktime/
Apple iTunes Home Page
http://www.apple.com/itunes/
http://www.apple.com/support/itunes/
Windows Media Player
http://www.microsoft.com/windows/windowsmedia/default.aspx
http://www.microsoft.com/windows/windowsmedia/player/11/security.aspx
http://www.microsoft.com/windows/windowsmedia/player/10/security.aspx
http://www.microsoft.com/technet/security/current.aspx
Adobe Flash Player Homepage
http://www.adobe.com/products/flashplayer/security/
http://www.adobe.com/downloads/updates/
Security Reports and Other Links
https://www2.sans.org/newsletters/risk/
http://findarticles.com/p/articles/mi_m0EIN/is_2006_Dec_18/ai_n16912185
General Networking Measures to Mitigate the Impact of Client-side Vulnerabilities:
- Users should be restricted from surfing any potentially dangerous URLs via URL blocking
- The Pentagon, for instance, has blocked access to all social networking sites like MySpace and YouTube.
- Deploy a commercial or an open-source URL filtering solution to prevent users visiting web sites serving exploits and malware.
Server-side Vulnerabilities in:
S1 Web Applications
S1.1 Description
Web-based applications such as Content Management Systems (CMS), Wikis, Portals, Bulletin Boards, and Discussion Forums are used by small and large organizations. A large number of organizations also develop and maintain custom-built web applications for their businesses (indeed, in many cases, such applications are the business). Every week hundreds of vulnerabilities are reported in commercially available and open source web applications, and are actively exploited. Please note that the custom-built web applications are also attacked and exploited even though the vulnerabilities in these applications are not reported and tracked by public vulnerability databases such as @RISK, CVE or BugTraq. The number of attempted attacks for some of the large web hosting farms range from hundreds of thousands to even millions every day.
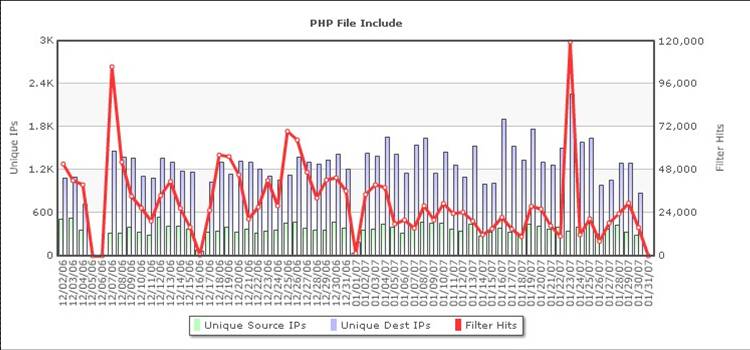
Number of PHP File Include attacks recorded at a web hosting facility by TippingPoint IPS
All web frameworks (PHP, .NET, J2EE, Ruby on Rails, ColdFusion, etc.) and all types of web applications are at risk from web application security defects, ranging from insufficient validation through to application logic errors. The most exploited types of vulnerabilities are:
- PHP Remote File Include: PHP is the most common web application language and framework in use today. By default, PHP allows file functions to access resources on the Internet using a feature called "allow_url_fopen". When PHP scripts allow user input to influence file names, remote file inclusion can be the result. This attack allows (but is not limited to):
- Remote code execution
- Remote root kit installation
- On Windows, complete system compromise may be possible through the use of PHP’s SMB file wrappers
- SQL Injection: Injections, particularly SQL injections, are common in web applications. Injections are possible due to intermingling of user supplied data within dynamic queries or within poorly constructed stored procedures. SQL injections allow attackers:
- To create, read, update, or delete any arbitrary data available to the application
- In the worst case scenario, to completely compromise the database system and systems around it
- Cross-Site Scripting (XSS): Cross site scripting, better known as XSS, is the most pernicious and easily found web application security issue. XSS allows attackers to deface web sites, insert hostile content, conduct phishing attacks, take over the user’s browser using JavaScript malware, and force users to conduct commands not of their own choosing - an attack known as cross-site request forgeries, better known as CSRF.
- Cross-site request forgeries (CSRF): CSRF forces legitimate users to execute commands without their consent. This type of attack is extremely hard to prevent unless the application is free of cross-site scripting vectors, including DOM injections. With the rise of Ajax techniques, and better knowledge of how to properly exploit XSS attacks, CSRF attacks are becoming extremely sophisticated, both as an active individual attack and as automated worms, such as the Samy MySpace Worm.
S1.2 How to Determine If You Are at Risk
Web scanning tools can help find these vulnerabilities, particularly if they are known bugs. However, to find all potential vulnerabilities requires a source code review as well as an application penetration test. These should be done by the developers prior to release of any important web application.
Inspect your web application framework's configuration and harden appropriately.
System administrators should consider scanning web servers periodically with vulnerability scanners, particularly if they run a large or diverse range of user-supplied scripts (such as on a hosting farm).
No person should be engaged to write web applications unless they can pass the GSSP Secure Software Programming exam that covers the essential security skills and knowledge that developers need to produce more secure applications.
S1.3 How to Protect against Web Application Vulnerabilities
From the PHP system administration and hosting perspective:
- Upgrade to PHP 5.2 as it eliminates many latent PHP security issues and allows for safer APIs, such as PDO
- Always test and deploy patches and new versions of PHP as they are released
- Frequent web scanning is recommended in environments where a large number of PHP applications are in use
- Consider using the following PHP configuration:
- register_globals (should be off, will break insecure apps)
- allow_url_fopen (should be off, will break apps that rely on this feature, but protect against a very active exploit vector)
- magic_quotes_gpc (should be off, will break older insecure apps)
- open_basedir (should be enabled and correctly configured)
- Consider using least privilege execution features like PHPsuexec or suPHP
- Consider using Suhosin to control the execution environment of PHP scripts
- Use Intrusion Prevention/Detection Systems to block/alert on malicious HTTP requests. Consider using Apache's mod_security to block known PHP attacks
- As a last resort, consider banning applications which have a track record of active exploitation, and slow response times to fix known security issues.
From the developer perspective:
- If you use PHP, migrate your application to PHP 5.2 as a matter of urgency.
- To avoid the coding issues above:
- Develop with the latest PHP release and a hardened configuration (see above)
- Validate all input according to the variable type it is being assigned
- Encode all output using htmlentities() or a similar mechanism to avoid XSS attacks
- Migrate your data layer to PDO - do not use the old style mysql_*() functions as they are known to be faulty
- Do not use user-supplied input with file functions to avoid remote file inclusion attacks
- Join secure coding organizations, such as OWASP (see references) to boost skills, and learn about secure coding
- Test your apps using the OWASP Testing Guide with tools like WebScarab, Firefox's Web Developer Toolbar, Greasemonkey and the XSS Assistant
- Measure your skill using the GSSP exams and fill in the gaps in your knowledge.
S1.4 References
OWASP - Open Web Application Security Project
http://www.owasp.org
OWASP Testing Guide
http://www.owasp.org/index.php/OWASP_Testing_Guide_v2_Table_of_Contents
OWASP Guide - a compendium of secure coding
http://www.owasp.org/index.php/Category:OWASP_Guide_Project
OWASP Top 10 - Top 10 web application security weaknesses
http://www.owasp.org/index.php/Top_10_2007
Suhosin, a Hardened PHP project to control the execution environment of PHP applications
http://www.hardened-php.net/suhosin/
PHPSecInfo
http://phpsec.org/projects/phpsecinfo/index.html
GSSP Exam blueprints and testing schedule
http://www.sans.org/gssp
S2. Windows Services
S2.1 Description
The family of Windows Operating systems supports a wide variety of services, networking methods and technologies. Many of these components are implemented as Service Control Programs (SCP) under the control of Service Control Manager (SCM), which runs as "services.exe". Vulnerabilities in the services that implement these operating system functions are some of the most common avenues for exploitation. When you first install Microsoft Windows Server 2003, Microsoft Windows XP, or Windows Vista some services are installed and configured to run by default whenever the computer is restarted. On Windows Server 2003 the specific services enabled with correspond to the role that is assigned to each server. You may not need all of the default services in your environment, and you should disable any unneeded services to enhance security. A service must log on to access resources and objects in the operating system, and most services are not designed to have their default logon account changed. If you change the default account password, the service will probably fail. If you select an account that does not have permission to log on as a service, the Microsoft Management Console (MMC) Services snap-in automatically grants that account the ability to log on as a service on the computer. However, this automatic configuration does not guarantee that the service will start. Windows Operating Systems include three built-in local accounts that are used as the logon accounts for various system services:
Local System account. The Local System account is a powerful account that has full access to the computer and acts as the computer on the network. If a service uses the Local System account to log on to a domain controller, that service has access to the entire domain. Some services are configured by default to use the Local System account, and this should not be changed. The Local System account does not have a user-accessible password.
Local Service account. The Local Service account is a special, built-in account that is similar to an authenticated user account. It has the same level of access to resources and objects as members of the Users group. This limited access helps safeguard your computer if individual services or processes are compromised. Services that use the Local Service account access network resources as a null session with anonymous credentials. The name of this account is NT AUTHORITY\Local Service, and it does not have a user-accessible password.
Network Service account. The Network Service account is also a special, built-in account that is similar to an authenticated user account. Like the Local Service account, it has the same level of access to resources and objects as members of the Users group, which helps safeguard your computer. Services that use the Network Service account access network resources with the credentials of the computer account. The name of the account is NT AUTHORITY\Network Service, and it does not have a user-accessible password.
Graphical user interface (GUI) - based tools can help you edit services. However, versions of these tools that were included with earlier versions of the Windows operating system (before Windows Server 2003) automatically apply permissions to each service when you configure any of the properties of a service. Tools such as the Group Policy Object Editor and the MMC Security Templates snap-in use the Security Configuration Editor DLL to apply these permissions. For example, when you use the MMC Security Templates snap-in to configure the startup state of a service in Windows XP, the following dialog box will display:
Figure 1. Services Security Dialog Box
Regardless of whether you click OK or Cancel, the permissions will be applied to the service that is being configured. Unfortunately, the permissions that this dialog box proposes do not match the default permissions for most services that are included with Windows. In fact, the permissions will cause a variety of problems for many services. We suggest you not alter the permissions on services that are included with Windows XP or Windows Server 2003 because the default permissions are already quite restrictive. You have several options to deal with this scenario:
- Use the Security Configuration Wizard, an optional Windows component that is included with Windows Server 2003 Service Pack 1 (SP1). Use this approach when you need to configure services and network port filters for various Windows Server 2003 server roles.
- Run the MMC Security Template snap-in and Group Policy Object Editor on a server that runs Windows Server 2003 with SP1. Use this approach when you need to configure services for security templates or Group Policies that will be applied to Windows XP.
- Use a text editor such as Notepad to edit the security templates or Group Policies on a computer that runs Windows XP Professional. This method is the least desirable, but some organizations or users may have no choice.
Several of the core system services provide remote interfaces to client components through Remote Procedure Calls (RPC). They are mostly exposed through named pipe endpoints accessible through the Common Internet File System (CIFS) protocol, well known TCP/UDP ports and in certain cases ephemeral TCP/UDP ports. Historically, there have been many vulnerabilities in services that can be exploited by anonymous users. When exploited, these vulnerabilities afford the attacker the same privileges that the service had on the host.
S2.2 Operating Systems Affected
Windows XP Home and Professional, Windows 2003 and Windows Vista are all potentially vulnerable.
S2.3 CVE Entries
CVE-2007-0213, CVE-2007-1748, CVE-2007-0938, CVE-2006-5584, CVE-2006-5583, CVE-2006-4691
CVE-2006-0027, CVE-2006-1314, CVE-2006-2370, CVE-2006-2371, CVE-2006-3439
S2.4 How to Determine If You Are at Risk
- Use any vulnerability scanner to check whether your systems are patched against these vulnerabilities. You can also consider using the Microsoft Windows Server Update Services (WSUS), Microsoft Baseline Security Analyzer (MBSA), Windows Live Scanner or Systems Management Server (SMS) to check the security patch status of your systems.
- Verify the presence of a patch by checking the registry key mentioned in the Registry Key Verification section of the corresponding security advisory. Additionally, it is advisable to also make sure the updated file versions mentioned in the advisory are installed on the system.
- To check if your system is vulnerable to an issue in an optional service, you need to determine if the service is enabled. This can be done through the Service Manager interface, which can be invoked from Services in Administrative Tools.
S2.5 How to Protect against Windows Services Vulnerabilities
- US Government users of Windows are now required to use the Federal Desktop Core Configuration for Windows XP or Vista. (http://fdcc.nist.gov/ ) Other organizations will find the FDCC to be a reliable and safe configuration, as well.
- Enable the Windows Firewall and/or install a 3rd party firewall on the host. Ensure that rules are applied to restrict access to the Windows machine except for those connections that are explicitly required. For example many of these vulnerabilities are found on interfaces offered through CIFS, and blocking ports 139/tcp and 445/tcp is essential for preventing remote attacks. It is also a good practice to block inbound RPC requests from the Internet to ports above 1024 to block attacks to other RPC based vulnerabilities. In enterprise environments the host Windows Firewall can be configured by General Policy Objects via Microsoft Active Directory.
- For Windows 2003 SP1 and R2 utilize the Security Configuration Wizard wherever possible in concert with the Windows firewall to reduce attack surface
- Utilize egress (as well as ingress) filtering on external network firewalls as part of defense-in-depth architecture to reduce threats of external as well as internal attack.
- Keep the systems updated with all the latest patches and service packs as part of defense-in-depth architecture. If possible enable Automatic Updates on all systems.
- Use intrusion prevention/detection systems at the network and host level as part of defense-in-depth architecture to prevent/detect attacks exploiting these vulnerabilities.
- Eliminate exposure to vulnerabilities by disabling the unneeded services. For Windows clients (XP, 2003 and/or Vista), the following services should generally be disabled:
| Service name | Display name | Enterprise Client desktop/laptop | Standalone desktop/laptop |
|---|---|---|---|
| Alerter | Alerter | Disabled | Disabled |
| ClipSrv | ClipBook | Disabled | Disabled |
| Browser | Computer Browser | Not Defined | Disabled |
| Fax | Fax | Not Defined | Disabled |
| MSFtpsvr | FTP Publishing | Disabled | Disabled |
| IISADMIN | IIS Admin | Disabled | Disabled |
| cisvc | Indexing Service | Not Defined | Disabled |
| Messenger | Messenger | Disabled | Disabled |
| mnmsrvc | NetMeeting® Remote Desktop Sharing | Disabled | Disabled |
| RDSessMgr | Remote Desktop Help Session Manager | Not Defined | Disabled |
| RemoteAccess | Routing and Remote Access | Disabled | Disabled |
| SNMP | SNMP Service | Disabled | Disabled |
| SNMPTRAP | SNMP Trap Service | Disabled | Disabled |
| SSDPSrv | SSDP Discovery Service | Disabled | Disabled |
| Schedule | Task Scheduler | Not Defined | Disabled |
| TlntSvr | Telnet | Disabled | Disabled |
| TermService | Terminal Services | Not Defined | Disabled |
| Upnphost | Universal Plug and Play Device Host | Not Defined | Disabled |
| W3SVC | World Wide Web Publishing | Disabled | Disabled |
Table 1. Disabled Windows Services on Windows Clients
Earlier versions of the operating system, especially Windows NT and Windows 2000, enabled many of these services by default for user convenience . These non essential services increase the exploitable surface significantly. For Windows machines that are used as servers (i.e. Print Server, File Server) refer to the appropriate configuration guides listed as references below and/or use automated tools such as the Windows 2003 Security Configuration Wizard to configure the services appropriately.
In some cases, null session access to the vulnerable interface could be removed as a work-around. It is a good practice to review your current RestrictAnonymous settings and keep them as stringent as possible based on your environment. http://www.securityfocus.com/infocus/1352
S2.6 References
Threats and Countermeasures: Security Settings in Windows Server 2003 and Windows XP
http://www.microsoft.com/technet/security/topics/serversecurity/tcg/tcgch00.mspx
Windows XP Security Guide
http://www.microsoft.com/technet/security/prodtech/windowsxp/secwinxp/default.mspx
Windows Server 2003 Security Guide
http://www.microsoft.com/technet/security/prodtech/windowsserver2003/w2003hg/sgch00.mspx
Using Windows Firewall
http://www.microsoft.com/windowsxp/using/networking/security/winfirewall.mspx
Security Configuration Wizard for Windows Server 2003
http://www.microsoft.com/windowsserver2003/technologies/security/configwiz/default.mspx
How to use IPSec IP filter lists in Windows 2000
http://support.microsoft.com/kb/313190
How to block specific network protocols and ports by using IPSec
http://support.microsoft.com/kb/813878
How to configure TCP/IP filtering in Windows 2000
http://support.microsoft.com/kb/309798
S3. UNIX/Mac OS Services
S3.1 Description
Most Unix/Linux systems include multiple standard services in their default installation. Mac OS X often suffers from the same vulnerabilities as Unix systems, since it is based on Unix. Unnecessary services should be disabled, and all servers facing open networks should be protected by a firewall.
For services which provide remote login and/or remote service, traffic cannot be simply blocked by firewalls. Buffer overflow vulnerabilities and flaws in authentication functions can often allow a vector for arbitrary code execution, sometimes with administrative privileges, so gathering vulnerability information and patching rapidly are very important. Every year, buffer overflow vulnerabilities in Unix/Linux services are found.
These services, even if fully patched, can be the cause of unintended compromises. Brute-force attacks against remote services such as SSH, FTP, and telnet are still the most common form of attack to compromise servers facing the Internet. Over the last couple of years a concerted effort has been made by attackers to recover passwords used by these applications via brute-force attacks. Increasingly worms and bots have brute-force password engines built into them. Systems with weak passwords for user accounts are actively and routinely compromised; often privilege escalations are used to gain further privileges, and rootkits installed to hide the compromise. It is important to remember that brute forcing passwords can be a used as a technique to compromise even a fully patched system.
Security-conscious administrators should use SSH or another encrypted protocol as their method of interactive remote access. If the version of SSH is current and it is fully patched, the service is generally assumed to be safe. However, regardless of whether it is up to date and patched SSH can still be compromised via brute-force password-guessing attacks. Use public key authentication mechanism for SSH to thwart such attacks. For the other interactive services, audit passwords to ensure they are of sufficient complexity to resist a brute-force attack.
Minimizing the number of running services on a host will also make it more secure. Many services have been used to further exploits and some combinations of services (such as web servers and FTP servers that share published directories) are particularly prone to exploits.
S3.2 Affected OSs
All versions of Unix/Linux/Mac OS Server are potentially at risk from improper and default configurations. All those OS versions may be affected by accounts having weak or dictionary-based passwords for authentication.
S3.3 CVE Entries
Remote services
CVE-2006-5815,
CVE-2007-0882,
CVE-2007-2446,
CVE-2007-0731,
CVE-2007-2791,
CVE-2007-1654
Kernel/Libraries
CVE-2007-4995,
CVE-2007-5191,
CVE-2006-6652,
CVE-2007-3641,
CVE-2007-5079,
CVE-2007-1351
Management Console/Tools
CVE-2007-3093,
CVE-2007-3094,
CVE-2007-3260,
CVE-2007-3232,
CVE-2007-2282,
CVE-2007-0980
Others
CVE-2007-2173,
CVE-2006-5616
S3.4 How to Determine If You Are Vulnerable
Default installations (either from the manufacturer or by an administrator) of operating systems or network applications may include a wide range of unneeded and unused services. In many cases the uncertainty about operating system or application needs leads many manufacturers or administrators to install a large amount of software in case it is needed in the future. This simplifies the installation process significantly but also introduces a wide range of unneeded services and user accounts that have default, weak, or known passwords.
The use of an updated vulnerability scanner or a port mapper can be highly effective in discovering any potential vulnerabilities left by default installations, such as unneeded and/or outdated services or applications. Also, a password cracker can help to avoid the use of weak or easily compromised passwords.
Note: never run a password cracker/vulnerability scanner, even on systems for which you have root-like access, without explicit, written permission from your employer. Administrators with the most benevolent of intentions have been fired and prosecuted for running password cracking tools without the authority to do so.
S3.5 How to Protect Against These Vulnerabilities
Disable unnecessary services
- Scan the server with a port scanner or vulnerability assessment tool to determine what unnecessary services are running on a system. Disable the services that are not required by any necessary applications.
- Establish and enforce reliable patch management procedures
- Install the latest vendor patches regularly to mitigate vulnerabilities in exposed services. Patch management is a critical part of the risk management process.
- Patch management tools are useful to find unpatched systems. Especially in a network where a lot of servers run, patching all servers is important, since only one unpatched server makes your network exploitable.
Use secure configuration
- Use the Center for Internet Security benchmarks from www.cisecurity.org for your OS and services you use. Also consider using Bastille (www.bastille-linux.org) to harden Linux and HP-UX based hosts.
- Consider moving services from default ports where possible. Automated scanners tend to only scan default ports.
- Ensure services are protected by vendor-supplied security mechanisms (for example SELinux or address space randomization).
Improve perimeter defense/monitoring log
- Deploy hardware/software firewall and IDS/IPS to detect and block attacks and protect required services. If possible, limit the source IP addresses for remote logins and services.
- In a mission critical network, use real-time log monitoring to find evidence of attacks. Log management and SIM tools are useful for real-time analysis of several kinds of logs.
Block brute force attacks
- Don't use default passwords on any account.
- Enforce a strong password policy. Don't permit weak passwords or passwords based on dictionary words.
- Audit to ensure your password policy is being adhered to.
- Limit the number of failed login attempts to exposed services.
- Limit the accounts that can log in over the network; root should not be one of them.
- Prohibit shared accounts and don't use generic account names like tester, guest, sysadmin, admin, etc.
- Log failed login attempts. A large number of failed logins to a system may require a further check on the system to see if it has been compromised.
- Consider using certificate based authentication.
- If your Unix system allows the use of PAM authentication modules, implement PAM modules that check the password's strength.
Avoid service interactions and misconfigurations
- Where possible, limit the functions of the host. Misconfigurations in multiple services may often increase the risk to a service.
S3.6 References
Brute Force Attacks and Counter Measures
http://isc.sans.org/diary.php?storyid=1541
http://isc.sans.org/diary.php?storyid=1491
http://isc.sans.org/diary.html?storyid=3212
http://isc.sans.org/diary.html?storyid=3209
http://isc.sans.org/diary.php?date=2006-08-01
General UNIX Security Resources
http://www.cisecurity.org
http://www.bastille-linux.org
http://www.puschitz.com/SecuringLinux.shtml
S4. Backup Software
S4.1 Description
Backup software is an extremely valuable asset for any organization. Backup software typically runs on many systems throughout an enterprise. In recent years, the trend has been to consolidate backup functions onto few servers, or even a single server. The hosts requiring backup services communicate with the backup server via the network. Interaction with the server generally conforms to a push approach, where the client sends data to the server to be backed up, or a pull approach, where the server polls for new data to be backed up from the client, or a combination of these two approaches. During 2007 many critical backup software vulnerabilities were discovered. Since the backup software generally runs with high privileges to read all files on a system, vulnerabilities in backup software have led to severe security vulnerabilities. Some of these vulnerabilities were exploited to completely compromise systems running backup servers and/or backup clients. Attackers leveraged these flaws for enterprise-wide compromise and obtained access to the sensitive backed-up data. Exploits have been publicly posted for many of these flaws, and these vulnerabilities are often exploited in the wild.
S4.2 Operating Systems and Backup Software Affected
All operating systems running backup server or client software are potentially vulnerable to exploitation. The affected operating systems tend to be Windows and Unix systems, as these systems form the preponderance of enterprise clients and servers.
The following popular backup software packages have had critical vulnerabilities:
- Computer Associates (CA) BrightStor ARCServe has had dozens of easy-to-exploit vulnerabilities with exploit code widely available.
- Symantec Veritas NetBackup/Backup Exec has had a few recently reported vulnerabilities.
- EMC Legato Networker also has had one publicly reported vulnerability.
S4.3 A Special Note on Backup Security
Backup data often contains all of, or at least large portions of, the data on a given system. Generally the backup data is stored in a centralized location and is often unencrypted. Physical security of backup media is of the utmost importance, as theft or analysis of backup media can provide complete access to critical data with little or no additional effort. If at all possible, backed up data should be encrypted with strong encryption, and the methods for decryption should be available only to trusted individuals.
S4.4 CVE Entries
CVE-2007-5332, CVE-2007-5330, CVE-2007-5328,, CVE-2007-5327,, CVE-2007-5325,, CVE-2007-5006,, CVE-2007-5004,, CVE-2007-5003, CVE-2007-3825, CVE-2007-3216, CVE-2007-2864, CVE-2007-2863, CVE-2007-2139,, CVE-2007-1447,, CVE-2007-5126, CVE-2007-3509, CVE-2007-2279, CVE-2007-3618
S4.5 How to Determine If You Are Vulnerable
- Use any vulnerability scanner to detect vulnerable backup software installations.
- Update your backup software to the latest version. Monitor your backup software vendor site and subscribe to the patch notification system if they have one, and to general security related sites such as US-CERT , SANS Internet Storm Center or new vulnerability announcements relating to your chosen backup software.
- Check for access to the TCP and UDP ports used by your backup software. The backup products listed above are known to use the following ports:
- Symantec Veritas Backup Exec
- TCP/10000 TCP/8099, TCP/6106, TCP/13701, TCP/13721 and TCP/13724 (A listing of ports used by Veritas backup daemons is available here.)
- CA BrightStor ARCServe Backup Agent
- TCP/6050, UDP/6051, TCP/6070, TCP/6503, TCP/41523, UDP/41524
- Sun and EMC Legato Networker
- TCP/7937-9936
S4.6 How to Protect against These Vulnerabilities
- Ensure the latest vendor supplied software patches are installed on the clients and servers.
- The ports being used by backup software should be firewalled from any untrusted network, especially the Internet.
- Data should be encrypted when stored on backup media and while being transported across the network.
- Host- or network-based firewalls should be run to limit the accessibility of a system's backup software to ensure that only the appropriate backup hosts can communicate on the backup server ports.
- Segregate your network to create a separate backup network VLAN.
- Backup media should be stored, tracked and monitored like other IT assets to deter and detect theft or loss.
- Backup media should be securely erased, or physically destroyed at the end of its useful life.
S5. Anti-virus Software
S5.1 Description
Anti-virus software is seen as a required basic tool within the "defense-in-depth" toolbox to protect systems today. Anti-virus software is now installed on almost all desktops, servers and gateways to combat virus outbreaks.
During 2007, attackers have shifted their focus to exploit security products used by a large number of end users. This includes anti-virus and personal firewall software. The discovery of vulnerabilities in anti-virus software is not limited to desktop and server platforms: gateway solutions are also affected, and compromising a gateway could cause a much larger impact since the gateway is the outer layer of protection and the only protection against some threats in many small organizations.
Multiple remote code execution vulnerabilities have been discovered in the anti-virus software provided by various vendors including Symantec, F-Secure, Trend Micro, McAfee, Computer Associates, ClamAV and Sophos. These vulnerabilities can be used to take a complete control of the user's system with limited or no user interaction.
Anti-virus software has also been found to be vulnerable to "evasion" attacks. By specially crafting a malicious file (for instance, an HTML file with an executable header) it may be possible to bypass anti-virus scanning. These evasion attacks can be exploited to create a vector for malware propagation, or bypass systems that would otherwise limit malware propagation.
S5.2 Operating Systems Affected
Any system with an installed anti-virus application or scanning engine meant to scan for malicious data could be affected. This includes solutions installed on desktops, servers and gateways. Any platform could be affected, including all Microsoft Windows and Unix systems.
S5.3 CVE Entries
Avast!
CVE-2007-2845, CVE-2007-2846, CVE-2007-1672AVIRA
CVE-2007-2974, CVE-2007-2973, CVE-2007-2972, CVE-2007-1671BitDefender
CVE-2007-0391ClamAV
CVE-2007-4560, CVE-2007-3023, CVE-2007-2029, CVE-2007-1997, CVE-2007-1745Computer Associates
CVE-2007-2864, CVE-2007-2523, CVE-2007-2522HAURI
CVE-2006-0864F-Secure
CVE-2007-3300, CVE-2007-2967, CVE-2007-2966, CVE-2007-2965, CVE-2007-1557Kaspersky
CVE-2007-3675, CVE-2007-1879, CVE-2007-1112, CVE-2007-0445, CVE-2007-1281Mcafee
CVE-2007-2152, CVE-2007-1538Panda
CVE-2007-3969, CVE-2007-3026, CVE-2007-1670Sophos
CVE-2006-6335, CVE-2006-0994Symantec
CVE-2007-3699, CVE-2007-0447, CVE-2007-3802, CVE-2007-3095, CVE-2007-3021Trend Micro
CVE-2007-1591, CVE-2007-0856, CVE-2007-0851S5.4 How to Determine If You Are Vulnerable
If you are running any release of any anti-virus software that has not been updated to the latest version, you are likely to be affected.
S5.5 How to Protect against Anti-virus Software Vulnerabilities
- Ensure that all of your anti-virus software is regularly and automatically updated.
- Regularly check your vendor website for upgrades, patches and security advisories. A list of anti-virus vendors is provided in the References below. The list may not be exhaustive.
- If you have deployed anti-virus software on gateway and desktops, use different anti-virus vendor solutions for gateway and desktop. If one is vulnerable, it will not create a single point of failure.
S5.6 References
Below is a list of anti-virus vendors to check for upgrades, patches and security advisories.
Anti-virus Security Advisories
- https://www2.sans.org/newsletters/risk/display.php?v=6&i=29#widely7 (Symantec)
- https://www2.sans.org/newsletters/risk/display.php?v=6&i=23#widely3 (F-Secure)
- https://www2.sans.org/newsletters/risk/display.php?v=6&i=9#widely2 (Trend Micro)
- https://www2.sans.org/newsletters/risk/display.php?v=6&i=17#07.17.29 (McAfee)
- https://www2.sans.org/newsletters/risk/display.php?v=6&i=24#widely2 (Computer Associates)
- https://www2.sans.org/newsletters/risk/display.php?v=6&i=9#widely6 (ClamAV)
- https://www2.sans.org/newsletters/risk/display.php?v=6&i=22#other1 (Avast!)
- http://www.sans.org/newsletters/risk/display.php?v=4&i=34#other2 (HAURI)
- https://www2.sans.org/newsletters/risk/display.php?v=5&i=19#widely6 (Sophos)
- https://www2.sans.org/newsletters/risk/display.php?v=6&i=31#widely4 (Panda)
- https://www2.sans.org/newsletters/risk/display.php?v=6&i=23#other1 (AVIRA)
- https://www2.sans.org/newsletters/risk/display.php?v=6&i=15#widely3 (Kaspersky)
Anti-virus Evasion Issues
- http://www.kb.cert.org/vuls/id/968818
- http://www.sans.org/newsletters/risk/display.php?v=4&i=43#other4
Other Anti-virus Resources
- http://www.cert.org/other_sources/viruses.html
- http://www.virusbtn.com/
- http://www.eicar.com/
- http://www.wildlist.org/
S6. Management Servers
S6.1 Description
Applications such as on-server virus and spam filters, directory servers, and management and monitoring systems pose a unique security challenge; in addition to opportunities for compromising the system hosting them, they provide opportunities to attack other systems.
S6.2 Applications Affected
These applications can be divided into multiple categories:
- Directory Servers - Used to maintain user and system information. Compromising these applications can give access to large amounts of information, including usernames and (possibly encrypted) passwords.
- Monitoring Systems - Used to monitor various other systems. These applications often have user accounts on monitored clients, allowing an attacker easy access to client systems.
- Configuration and Patch Systems - These systems are used to maintain client configurations and patches. Compromising these systems provides an easy path to further distribute malware.
- Spam and Virus Scanners - Vulnerabilities in these systems can often be exploited with little or no user interaction, by simply sending a specially-crafted email message. Once compromised, attackers can more easily send spam and virus-containing emails. Additionally, these systems often contain vital information, such as users' mailboxes.
These applications run on a variety of operating systems, including Microsoft Windows, Solaris, HP-UX, Novell Netware, and others.
S6.3 CVE Entries
CVE-2006-5478, CVE-2006-4509, CVE-2006-4510, CVE-2006-4177, CVE-2006-2496, CVE-2006-0992, CVE-2005-3653, CVE-2005-1928, CVE-2005-1929
S6.4 How to Determine If You Are at Risk
- Use a vulnerability scanner.
- Track vendor security announcements.
S6.5 How to Protect Against These Vulnerabilities
- Keep the systems updated with all the latest patches and service packs. if provided, use an automatic update system.
- Use Intrusion Prevention/Detection Systems to prevent/detect attacks exploiting these vulnerabilities.
- Ensure that only authorized users and systems have access to the affected systems.
S6.6 References
Trend Micro ServerProtect Multiple Vulnerabilities
http://archives.neohapsis.com/archives/vulnwatch/2005-q4/0066.html
http://archives.neohapsis.com/archives/vulnwatch/2005-q4/0067.html
http://archives.neohapsis.com/archives/vulnwatch/2005-q4/0068.htmlTrend Micro Home Page
http://www.trendmicro.com/CA iTechnology iGateway Buffer Overflow
http://supportconnectw.ca.com/public/ca_common_docs/igatewaysecurity_notice.aspCA Home Page
http://www.ca.com/Novell eDirectory iMonitor Remote Buffer Overflows
http://www.zerodayinitiative.com/advisories/ZDI-06-016.htmlNovell Home Page
http://www.novell.comSymantec Sygate Management Server SQL Injection
http://securityresponse.symantec.com/avcenter/security/Content/2006.02.01.htmlSymantec Home Page
http://www.symantec.com/HP OpenView Multiple Remote Command Execution
http://h20000.www2.hp.com/bizsupport/TechSupport/Document.jsp?objectID=c00672314
http://h20000.www2.hp.com/bizsupport/TechSupport/Document.jsp?objectID=c00671912HP OpenView Storage Data Protector Remote Code Execution
http://archives.neohapsis.com/archives/bugtraq/2006-08/0273.htmlHP OpenView Home Page
http://h20229.www2.hp.com/Barracuda Spam Firewall Remote Command Injection
http://archives.neohapsis.com/archives/bugtraq/2006-08/0093.htmlBarracuda Home Page
http://www.barracudanetworks.com/ns/?L=enS7. Database Software
S7.1 Description
Databases provide the ability to store, search and manipulate large amounts of data. They are key elements of many systems, even though their presence may not be directly visible to users. They are found in many common applications including financial, banking, customer relationship management and system monitoring software.
Due to the valuable information they often store, such as personal and financial details, databases are often a target of attack and are of particular interest to identity thieves. Database systems are often very complex, combining the core database with a collection of applications. Some of these applications are supplied by the database vendor, others (such as web applications) are written by users in house. A flaw in any of these components can compromise the stored data. It is not sufficient to protect the database alone, all the associated applications need to be secured. The most common vulnerabilities in database systems are:
- Use of default configurations with default user names and passwords.
- SQL Injection via the database's own tools, third part applications or web front-ends added by users. Huge numbers of vulnerabilities in this class are announced every year.
- Use of weak passwords for privileged accounts.
- Buffer overflows in processes that listen on well known ports.
Many different database systems are available. Some of the most common are Microsoft SQL Server (proprietary, runs on Windows), Oracle (proprietary, runs on many platforms), IBM DB2 and IBM Informix (both proprietary, run on multiple platforms), Sybase (proprietary, runs on many platforms), MySQL and PostgreSQL (both open source and available on many platforms).
All modern databases can be accessed over networks, which means that anyone with network access and readily available query tools can attempt to connect directly to the database. The commonly used default connections are: Microsoft SQL via TCP port 1433 and UDP port 1434, Oracle via TCP port 1521, IBM DB2 via ports 523 and 50000 up, IBM Informix via TCP ports 9088 and 9099, Sybase via TCP 4100 or 2025, MySQL via TCP port 3306, and PostgreSQL via TCP port 5432.
Due to the network connections they provide, databases may suffer from worms; there have been examples of worms attacking Microsoft SQL and Oracle.
In addition to addressing the specific vulnerabilities mentioned here, administrators concerned with database security should consider:
- The impact of standards such as the Payment Card Industry Data Security Standard that may require encryption of some information such as credit card numbers or prohibit the storage of some types of information.
- The risks of transferring entire databases or large quantities of data onto mobile devices: there have been numerous reports of personal data being lost through the theft of laptops.
S7.2 Operating Systems Affected
Most database systems, commercial and open source, run on multiple platforms. Issues regularly cover all supported platforms.
S7.3 CVE Entries
These are the entries released since September 2006 that have a CVSS base score of 7 or more. Earlier vulnerabilities can be found in previous editions of this SANS document. In many cases reported issues are not flaws in the databases themselves but in applications built around them, e.g. SQL injection into web interfaces; these have not been included here.
IBM DB2
CVE-2007-1086, CVE-2007-1087, CVE-2007-1088, CVE-2007-1089, CVE-2007-2582, CVE-2007-5652.
IBM Informix
None during this reporting period.
Microsoft SQL Server
MySQL
None during this reporting period.
Oracle
CVE-2006-5332, CVE-2006-5333, CVE-2006-5334, CVE-2006-5335, CVE-2006-5336, CVE-2006-5339, CVE-2006-5340, CVE-2006-5341, CVE-2006-5342, CVE-2006-5343, CVE-2006-5344, CVE-2006-5345, CVE-2006-7138, CVE-2007-0272, CVE-2007-1442, CVE-2007-2113, CVE-2007-2118, CVE-2007-5506.Note: Oracle releases quarterly Critical Patch Updates (CPU) covering large numbers of issues in the database and associated applications. The list above contains vulnerabilities in the core Oracle database programs for which there is specific information. There are many other vulnerabilities about which there is no public information other than the advice to apply the CPU.
PostgreSQL
Note: other issues have been recorded in vulnerability lists as a result of a white paper on PostgreSQL security, but the developers argue that these are not security issues.
Sybase
None during this reporting period.
S7.4 How to Determine If You Are Vulnerable
It is not sufficient to check a simple, manually maintained list of the applications that have been installed. Because databases are often distributed as components of other applications, it is possible for a database to be installed without administrators realizing it. Databases may therefore remain unpatched or in vulnerable default configurations.
Perform a vulnerability scan on systems to determine whether database software is available, accessible and vulnerable. In addition to general-purpose vulnerability scanners there are specialized tools, both commercial and public domain; a web search for "database security scanners" will identify possible tools. They vary from simple network service scanners, though systems that check for default configurations and passwords, to systems that check the detailed configurations of specific makes of databases.
S7.5 How to Protect Against Database Vulnerabilities
- Ensure that all DBMS patches are up to date. Unpatched or outdated versions are likely to include vulnerabilities. Check vendor sites for patch information. Remain up to date with the vulnerabilities and alerts announced by the vendors:
- IBM DB2 (http://www-306.ibm.com/software/data/db2/udb/support/)
- IBM Informix (http://www-1.ibm.com/support/docview.wss?rs=0&uid=swg24009130)
- Microsoft SQL (http://www.microsoft.com/technet/security/bulletin/notify.mspx)
- MySQL (http://lists.mysql.com/)
- Oracle Security Alerts (http://www.oracle.com/technology/deploy/security/alerts.htm)
- PostgreSQL (http://www.postgresql.org/support/security)
- Sybase (http://www.sybase.com/support)
- Ensure that the DBMS and applications have been secured:
- Remove/change default passwords on the database's privileged and system accounts before deploying the system on the network. Lists of default accounts are readily available on the Internet.
- Use minimal privileges.
- Use stored procedures where possible.
- Remove/disable unnecessary stored procedures.
- Set length limits on any form fields.
- See the references section below for several useful resources to help secure DBMS.
- Use firewalls or other network security devices to restrict network access to the ports associated with database services.
- A class of tool has become available that allows you to capture network traffic to a database and examine the structure of the SQL queries that are being made. These have a role in auditing, identifying the set of valid queries for an application and spotting unusual behaviour or common attack patterns. They can also be placed in line with the database to act as a form of application firewall or application specific intrusion detection and prevention system.
- Consider encrypting the communications between applications and the database.
- Do not trust user input! Ensure that the applications linked to databases clean all user input at the server side to avoid attacks such as SQL injection (see http://www.sans.org/reading_room/whitepapers/securecode/23.php)
S7.6 References
Generic and multiple database resources
- SANS reading room on database security: http://www.sans.org/reading_room/catindex.php?cat_id=3
- DoD database security technical implementation guide: http://iase.disa.mil/stigs/stig/index.html
- http://www.databasesecurity.com/
IBM DB2
IBM Informix
- http://www.databasesecurity.com/informix.htm
- http://publib.boulder.ibm.com/infocenter/idshelp/v10/index.jsp?topic=/com.ibm.admin.doc/admin197.htm
Microsoft SQL Security
- http://www.microsoft.com/sql/techinfo/administration/2000/security/default.mspx
- http://www.sqlsecurity.com/
- CIS SQL Server Benchmark Tool: http://www.cisecurity.org/bench_sqlserver.html
MySQL
- SecurityFocus step-by-step guide to securing MySQL: http://www.securityfocus.com/infocus/1726
- MySQL documentation, security section: http://dev.mysql.com/doc/refman/5.0/en/security.html
- Secure MySQL database design: http://www.securityfocus.com/infocus/1667
- MySQL security overview: http://www.devshed.com/c/a/MySQL/MySQL-Security-Overview/
- http://mysqlsecurity.com/
Oracle
- SANS Comprehensive Security Checklist for Oracle: http://www.sans.org/score/oraclechecklist.php
- http://www.oracle.com/technology/deploy/security/pdf/twp_security_checklist_db_database.pdf
- CIS benchmarktool: http://www.cisecurity.org/bench_oracle.html
- http://www.petefinnigan.com/orasec.htm,
http://www.petefinnigan.com/tools.htm - http://otn.oracle.com/deploy/security/index.html
- http://www.red-database-security.com/whitepaper/oracle_security_whitepaper.html
PostgreSQL Security Guide
Sybase
- Guide to Sybase security: http://www.niiconsulting.com/innovation/Sybase.pdf
Security Policy and Personnel:
H1. Excessive User Rights and Unauthorized Devices
H1.1 Introduction
Some attacks cannot be effectively prevented by technical controls alone. Unwary users can be enticed to do unsafe things. Clever users can find unsafe ways to get things done, unintentionally exposing their employers to multiple threats. To prevent such threats from exploiting these weaknesses, administrative controls are needed to supplement technical and physical controls.
In time, technical controls may be able to enforce policies that proscribe user behavior; but until this is achieved, periodic reviews are essential in order to ensure that administrative controls are effective. It is also essential to establish a process that will detect these violations and ensure that any non-compliant system is brought back to a state of compliance in an efficient manner.
H.1a Unauthorized and/or infected devices on network
The best efforts to secure an information system are futile if users connect unauthorized devices to the network or to a computer system. A rogue wireless access point can be an open door to any malicious individual wanting to gain access to the network. A personal laptop connected to a corporate network can introduce whatever malware infecting it onto the network. Unsecured corporate laptops that have been connected to an unsafe public networks will eventually bring back all the malware they have collected to be shared with the entire organization. Thousands of computers have been compromised by attacks where the laptop's owner is specifically targeted in order to infect the laptop with a Trojan horse that "calls home" once it has been connected to the corporate network. This allows an outsider full access into a previously secure network. The same goes for an outsider able to connect an unknown device onto the corporate network, this could simply be a laptop or a higher risk issue like a wireless access point.
Policies must address such issues as rogue devices and infected systems in order to ensure adequate protection of the corporate computing infrastructure, but without verification policies are usually ineffective. Network access control has become an important tool to address such issues. Continuous monitoring of data flows and network connections can immediately identify unauthorized devices. In addition, network access control systems can detect malware as well as ensure that patches and malware signatures are up to date. They can then segregate systems which do not meet the policy and place them in quarantine until they have met corporate standards defined in the policy.
H.1b Excessive User Rights and Unauthorized software
Unmanaged software introduces multiple risks for the corporation. That software may contain security vulnerabilities, and users may not be sufficiently informed or motivated to apply patches regularly. Furthermore users (or people using their computer without corporate approval like children or spouses) can install software which, without the users’ knowledge, contains malware which could lead to a network or data compromise. Users may also install software providing functionality (e.g. peer-to-peer file sharing) that invites new vulnerabilities into the network environment. Those responsible for information security should consider implementing policies, and associated detective and corrective controls, to mitigate such vulnerabilities.
Organizations are vulnerable if users are granted sufficient rights which allow them to install software themselves in an uncontrolled fashion. It can also lead to pirated software being installed on corporate systems which opens another range of issues from a legal perspective. In order to address this, it is essential to enforce a policy of limiting user rights to the least privilege required to perform job related duties. This will in fact eliminate issues relating to malware, potentially unwanted programs and pirated software being installed by the user himself.
H1.2 References
http://www.isaca.org/Template.cfm?Section=Home&CONTENTID=17170&TEMPLATE=/ContentManagement/ContentDisplay.cfm
http://technet2.microsoft.com/WindowsServer/en/library/e903f7a2-4def-4f5f-9480-41de6010fd291033.mspx?mfr=true
http://www.sans.org/resources/policies/Password_Policy.pdf
http://www.sans.org/resources/policies/Acceptable_Use_Policy.pdf
http://www.cerias.purdue.edu/weblogs/spaf/general/post-30/H2. Phishing/Spear Phishing
H2.1 Description
Online Identity Theft
Identity Theft is the phrase used to describe an action where a person uses the identity of another to fraudulently obtain credit, goods, services, or to commit crimes. Examples of these crimes are bank and credit card fraud, wire fraud, mail fraud, money laundering, bankruptcy fraud and computer crimes. With the advance of the Internet, the traditional fraud schemes became magnified, in particular with Online identity theft crimes.The word "phishing" was first used around 1996 when hackers began stealing America On-Line accounts by sending email to AOL users, that appeared to come from AOL. Phishing attacks now target users of online banking, payment services such as PayPal, online e-commerce sites, and web-based e-mail sites. Phishing attacks are growing quickly in number and sophistication. In fact, most major banks in the USA, the UK and Australia have been hit with phishing attacks.
Spear Phishing
Spear phishing is a highly targeted phishing attack. Spear phishers send e-mails that include information about staff or current organizational issues that make it appear genuine to employees or members within a certain company, government agency, organization, or group. The message may look like it comes from your employer or from a colleague who might send an e-mail message to everyone in the company, such as the head of human resources or the person who manages the computer systems, and could include requests for user names or passwords or tell recipients to download malicious attachments from an infected web site. Spear phishing has become one of the most damaging forms of attacks on military organizations in the US and other developed countries. Attackers gain user name and password information and then break in to ex filtrate sensitive military information.Voice Phishing
A newer form of phishing replaces a web site with a telephone number. In this form of phishing, an email tells you to call a specific number where an audio response unit, at the end of a compromised voice phone line, waits to take your account number, personal identification number, password, or other valuable personal data. The person/audio unit on the other end of the voice phone line might claim that your account will be closed or other problems could occur if you don't respond.H2.2 Affected Operating Systems
Phishing is a social engineering technique that targets users. While various application add-ons can provide some defense against phishing techniques, all operating systems can be considered equally affected because the attack target is the end user. There is a natural human instinct to trust; phishing attacks attempt to exploit this. While they leverage flaws in browsers, email systems, and DNS, they do so only to enhance the appearance of legitimacy: ultimately it is the end user that is tricked into providing information to the phishers.
H2.3 How to Determine if You Are at Risk
Phishing mostly uses social engineering techniques to ensure success. Awareness of such techniques can diminish the chance of being in risk of such attacks.
Identity thieves may also use computer intrusions into organisations such as online businesses to gather large amounts of credit card or other identification information. They may also attempt to harvest information that is available on public Internet sites; do not expose too much information about yourself or your family members (e.g. addresses and phone numbers) to community web sites such as MySpace, Orkut and Facebook
H2.4 How to Protect against Phishing Attacks
Since phishing attacks are aimed at users, user awareness is a key defense. The most promising method of stopping spear phishing is continuous periodic awareness training for all users; this may even involve mock phishing attempts to test awareness.
Less effective, but still valuable methods include:
- Do not mass e-mail your customer base with web links directed to your site or any other website. Doing so teaches your customer base to accept such emails as normal.
- Do not use your authentication credentials, or other non-public personal information, to authenticate your customer base.
- Log identifying information for any system changing user information online.
- Be sure to report all incidents of fraud to a law enforcement agency.
- Anti-Phishing Software: Applications that attempt to identify phishing content in both e-mail and web sites usually integrate with web browsers and e-mail clients. Several options exist:
- NetCraft Toolbar: available for both Internet Explorer and Firefox
- Google Safe browsing: available for Firefox
- Ebay Toolbar: available for Internet Explorer
- Earthlink Scamblocker: available for both Internet Explorer and Firefox
- Geotrust Trustwatch - available for Internet Explorer, Firefox, and Flock
- McAfee SiteAdvisor - available for Internet Explorer and Firefox
- User Education: One of the best strategies to combat phishing is to educate your users of current and all new phishing attack methods, and to make them knowledgeable on what to do in the event of a phishing attack.
- Two Factor Authentication: Include other non-password authentication mechanisms when possible.
H2.6 References
Anti-Phishing Working Group
http://www.antiphishing.org/3sharp study Gone Phishing: Evaluating Anti-Phishing Tools for Windows
http://www.3sharp.com/projects/antiphishing/gone-phishing.pdfVoIP Phishing Scams
http://blogs.pcworld.com/staffblog/archives/001921.htmlThe Ghost In The Browser; Analysis of Web-based Malware
http://www.usenix.org/events/hotbots07/tech/full_papers/provos/provos.pdfPhone phishing: The role of VoIP in phishing attacks
http://searchsecurity.techtarget.com/tip/0,289483,sid14_gci1193304,00.htmlPhishing and Spamming via IM (SPIM)
http://isc.sans.org/diary.html?storyid=1905Suspicious e-Mails and Identity Theft
http://www.irs.gov/newsroom/article/0,,id=155682,00.htmlH3. Unencrypted Laptops and Removable Media
H3.1 Description
Loss of laptops and removable media has become a major liability for corporations and government agencies as well as for general consumers. All too frequently, a major loss of personal or identifying information is traced back to the loss of a single laptop or piece of removable media.
In the past, personal data was stored in paper records or on centralized systems. With growth in computer storage, it is possible to store large amounts of personal information on laptops, desktops, or portable media. This portability places data at a greater risk of loss or compromise, both from malice and simple human forgetfulness. Since removable storage devices are designed specifically for portability, they also tend to be easy to lose or misplace.
Since portable storage devices are often shared between machines, they provide a potent vector for malware propagation. Users often share media between enterprise and personal systems, providing an obvious opportunity for viruses and other malware to spread between networks and physical locations.
Identities exposed by recent laptop losses:
Statistics from: http://www.privacyrights.org/ar/ChronDataBreaches.htmH3.2 How to Determine If You Are At Risk
Every company has some data that must be protected: trade secrets, personally identifying information about employees, human resources and payroll data, sales data, price sheets, contacts, customer databases, and so on. In the absence of active controls that ensure all portable devices and removable media are encrypted and accounted for, some risk of loss is present. Here are questions that can help determine the level of risk:
- What policy is in place regarding moving sensitive data onto removable media or portable computers?
- What encryption is installed and used on laptops, portable computers, and removable storage?
- What controls are in place to track access to sensitive data in order to determine inappropriate data transfer has taken place?
- What controls are in place to make sure all storage devices are shredded (or wiped) so the data is no longer accessible or recoverable when disposed of?
H3.3 Mitigation Strategies
- At the most basic level, a written security policy regarding portable computers and removable media is necessary. This policy should be reviewed and approved by senior management. If at all possible, the policy should mandate the encryption of all data on portable computers and removable media.
- Should a full encryption policy prove impossible, attempts should be made to provide file system or disk-level encryption for certain files. If such a strategy is employed, careful analysis must be undertaken: operating systems and applications often store working and temporary data in unusual locations that may be outside of the encrypted areas of the system. Care must be taken to avoid a false sense of security when only partial encryption is employed.
- There should be a clear policy as to which systems will have encryption: all systems or some subset of systems. The security policy should mandate that sensitive data is only placed on systems with effective encryption. Of course, some validation method should be employed to ensure that systems actually conform to the written security policy.
- Decryption methods and tools, including encryption keys, should be known to a limited set of individuals. However, under no circumstances should data decryption capability be limited to a single individual, as loss of that individual will be just as catastrophic as loss of the encrypted data. Encryption key sharing and escrow strategies should be employed.
- For removable media, the written security policy should dictate who may use such devices, the nature (type and sensitivity) of data that may be stored on them, if they may be taken outside of the enterprise environment, and possibly the specific types and models of removable media that may be used.
- Once a policy is in place, the organization should choose level and manner of compliance control to be implemented. This could range from no technical control (reliance on policy) up to the deployment of specific software packages and policies that restrict the ability to mount removable media.
- Safeguards should be in place to notify technical staff when sensitive data is transferred to removable systems or media. This is a non-trivial task and one that often helps drive the choice between full disk and partial disk encryption solutions.
- Often the loss of a device containing sensitive data is the fault of third parties such as contracting firms, rather than the enterprise that owns the data. To mitigate this risk add specific requirements for encryption of data and data storage to contracts with external firms that have access to sensitive data.
H3.4 References :
Use Group Policy to disable USB, CD-ROM and Floppy Disk
http://support.microsoft.com/kb/555324Listing of breaches of personal information
http://www.privacyrights.org/ar/ChronDataBreaches.htmListing of State Laws about disclosure after the loss of personally identifiable information (PII)
http://www.vigilantminds.com/files/vigilantminds_state_security_breach_legislation_summary.pdfLoss of Laptops
http://www.numbrx.net/2006/08/19/chevron-employees-data-lost-with-stolen-laptop/
http://www.caslon.com.au/datalossnote3.htm
http://privacy.med.miami.edu/learning_from_others.htm
http://wizbangblog.com/content/2007/08/02/laptop-theft-leaves-verisign-employees-data-exposed.php
http://seattlepi.nwsource.com/business/295769_boeing13.html
http://www.journalinquirer.com/site/news.cfm?newsid=18840780&BRD=985&PAG=461&dept_id=161556&rfi=6Loss of USB drives
http://www.fcw.com/article97113-12-18-06-Print
http://www.kristv.com/Global/story.asp?S=6667387
http://redtape.msnbc.com/2006/04/military_thumb_.html
http://www.securestix.com/bad_news.php
http://www.nytimes.com/2006/04/14/world/asia/14afghan.html?_r=2&oref=slogin&oref=sloginLoss of backup tapes
In February, Bank of America lost unencrypted backup tapes being shipped on a commercial airplane; data included details for more than a million customers.
http://tinyurl.com/4jvbzIn April, Iron Mountain lost its fourth shipment of backup tapes in 2005 - this time containing data about 600,000 current and former employees of Time Warner.
http://www.networkworld.com/news/2005/050605-timewarner.html?rlIn June, Citigroup announced that back-up tapes being sent via UPS were lost in transit; data including Social Security numbers on 3.9 million consumer lending customers were lost.
http://www.networkworld.com/news/2005/060605-citibank.html?rlIn November, Marriott International realized that some back-up tapes for its Vacation Club were missing; at the end of the year, it announced that the lost or stolen tapes contained credit-card and Social Security number data on 206,000 clients and also on some employees.
http://www.washingtonpost.com/wp-dyn/content/article/2005/12/27/AR2005122700959.htmlApplication Abuse:
A1. Instant Messaging
A1.1 Description
Instant messaging (IM) is increasingly being accepted as a legitimate method of communication for both personal and business use. IM applications are available on diverse platforms, ranging from traditional PC-based IM to Mobile IM on Personal Digital Assistants (PDAs) and Cell Phones. This widespread use of instant messaging, while convenient for users, can significantly increase the security risks for both organizations and individual users. Attacks include variants of e-mail worms spread through the use of instant messaging, new variations in the establishment and spread of botnets, and the use of compromised instant messaging accounts to lure users into revealing sensitive information.
The general risk areas related to instant messaging are:
- Malware -- Worms, viruses, and Trojans transferred through instant messaging. Many bots are controlled via IRC (instant message) channels.
- Information confidentiality -- Information transferred via instant messaging can be subject to disclosure at several points during the communication. The messages generally pass through networks and servers not under your control. Also, most IM programs now offer file sharing services. The process of file sharing may leave duplicates of confidential documents in shared folders of all participants after the IM session has been terminated.
- Network -- Denial of service attacks; excessive network capacity utilization, even through legitimate use.
- Application vulnerabilities -- Instant messaging applications may contain vulnerabilities that can be exploited to compromise affected systems. In addition to the IM application, possible vulnerabilities include errors in supporting software and improper interfaces with modules of supporting software. Some of the IM application functionality may rely on modules from other programs and the underlying operating system, inheriting vulnerabilities present in these programs. In addition, since only specific modules may be called, the security processes built into higher levels of the called support application may be bypassed, creating new attack vectors.
Mobile IM can present significant security risks beyond those associated with PC-based IM. Devices such as cell phones with IM capability often do not have password protection or encryption of locally stored data. The result is that masquerade attacks against e-mail and IM contacts are trivial to implement from lost Mobile IM devices. The wireless nature of mobile devices further complicates implementing proper mobile device security during IM sessions.
Popular instant message applications include: AOL Instant Messenger (AIM), Gaim, ICQ, Jabber Messenger, Lotus Sametime, Skype, QQ, Windows Live Messenger (WLM), Google Talk, Trillian and Yahoo! Messenger. Instant messaging protocols include: IRC, MSNP, OSCAR, SIMPLE, XMPP and YMSG.
A1.2 Affected Operating Systems
Instant messaging applications are available for all popular operating systems.
A1.3 CVE Entries
CVE-2007-1680, CVE-2007-2418, CVE-2007-2478, CVE-2007-2931, CVE-2007-3305, CVE-2007-3832, CVE-2007-3928, CVE-2007-4579
A1.4 How to Protect against IM Vulnerabilities and Unauthorized IM Usage
- Establish policies for acceptable use of instant messaging and ensure that all users are aware of those policies and clearly understand the potential risks.
- Establish policies for Mobile device usage, including password and encryption requirements.
- Create proper configuration standards for IM products that restrict file transfers.
- In general, users should not be permitted to install software. Restrict Administrative and Power User level privileges to support personnel acting in their support capacity. If a user must have Administrative or Power User privileges, create a separate account to be used for his/her daily office functions, Internet surfing and on-line communication.
- Ensure that vendor patches are promptly applied to instant messaging software, interrelated applications, and the underlying operating system.
- Employ anti-virus and anti-spyware products.
- Do not rely on external IM servers for internal use of instant messaging; Provide a commercial grade IM proxy or internal IM server.
- Create secure communications paths when using instant messaging with trusted business partners.
- Appropriately configure intrusion detection/prevention systems. Understand that many instant messaging applications are capable of enabling associated communications to masquerade as otherwise legitimate traffic (e.g. http).
- Deploy products specifically designed for instant messaging security.
- Filter all http traffic through an authenticating proxy server to provide additional capabilities of filtering/monitoring instant messaging traffic.
- Block access to known public instant messaging servers that have not been explicitly authorized. (Note: Offers only partial protection due to the number of potential external servers.)
- Block popular instant messaging ports. (Note: Offers only partial protection, due to the number of potential protocols and associated ports, and the ability of applications to bypass port restrictions.)
- Monitor using an Intrusion Detection/Prevention system for users creating tunnels for IM or bypassing proxies.
- Educate partners with whom you share files, and teach them to delete shared files after the IM session.
- Establish "Memorandum of Understanding" agreements with partners with whom you must share confidential documents, specifying non-disclosure responsibilities.
- Use access control such as passwords to protect group sessions and presentations.
A1.5 References
Phishers hijack IM accounts
http://news.com.com/Phishers+hijack+IM+accounts/2100-7349_3-6126367.htmlInstant messaging: a new target for hackers
http://www.leavcom.com/ieee_july05.htmAIM bot creates "fight combos" to spread
http://www.securityfocus.com/brief/305Secure Instant Messaging in the Enterprise
http://searchsecurity.techtarget.com/tip/0,289483,sid14_gci1199405,00.htmlRemote command execution, HTML and JavaScript injection vulnerabilities in AOL's Instant Messaging software
http://www.securityfocus.com/archive/1/480587A2. P2P File Sharing Applications
A2.1 Description
Peer to Peer networks consist of collections of computers or “nodes” that simultaneously function as both “clients” and “servers” to achieve a common purpose. The nodes may exchange data, share resources, provide directory services, support communications and provide real time collaboration tools.
Several control and communication architectures are utilized. Centralized index servers can provide directory services for data and service availability. In fully distributed networks each node helps with the indexing and directory services and is fully equivalent. Hybrid architectures combine the features of both to different degrees and groups of nodes may “elect/promote” certain nodes to act as regional index/directory servers.
Many legitimate applications use P2P. Software tool vendors, including Microsoft and Sun, provide a variety of tools and encourage development of P2P applications. However, like any data transfer tool, P2P applications can be misused or exploited to illegally share copyrighted material; obtain confidential data; expose users to unwanted pornography, violence or propaganda; distribute and execute malware (viruses, spyware, bots, etc.); overload the network; mine usage and behavior patterns; and control bots, all of which can create a legal liability. The liability and legal prosecution may not be limited to the perpetrator and may be extended to the network sponsor, supporters or members.
The P2P networks themselves may be attacked by modifying legitimate files with malware, seeding malware files into shared directories, exploiting vulnerabilities in the protocol or errors in coding, blocking (filtering) the protocol, denial of service by making the network function slowly, spamming and identity attacks that identify network users and harass them. Legal action has been successfully used to shut down some popular networks that were culprits of copyright infringement.
The Storm Worm uses eDonkey/Overnet Peer to Peer protocol to communicate with infected hosts. It is estimated to run on as many as 1,000,000 to 50,000,000 infected and compromised computer systems as of September 2007.
P2P concepts and techniques are evolving and can be found in:
- File sharing networks - whose main goal is to share resources such as storage and bandwidth. These operate through a distributed network of clients, sharing directories of files or entire hard drives of data. Clients participate by downloading files from other users, making their data available to others and coordinating file searches for other users.
- Cloud Computing - (Also called distributed processing, grid computing, mesh networks) where hundreds or thousands of computers are deployed to provide a virtual computing environment to accomplish a given task by distributing processing load and data. Cloud computing brings servers on-line as needed, and the end user does not know where the data resides or executes at any point. In some cases, the application runs on a combination of servers and on the user’s PC. Server clouds can reside physically in large facilities controlled by one organization or they can also reside all over the Internet. Because resizable computing capacity is based on virtual servers the data owner does not really know where his programs and data reside physically.
Most of the P2P programs use a set of default ports but they can automatically or manually be set to use different ports if necessary to circumvent detection, firewalls, or egress filters. The trend seems to be moving towards the use of http wrappers and encryption to easily bypass corporate restrictions.
A2.2 Operating Systems Affected
There are versions of P2P software available for all Microsoft Windows operating systems currently in use, along with versions for Linux, MacOS and most Unix-like Operating Systems.
A2.3 Detecting P2P activity
Detecting P2P activity on the network can prove to be challenging. It is possible to detect P2P software running on your network by:
- Monitoring traffic for certain TCP/UDP ports works well for older P2P programs. However, many P2P programs have moved on to using http, https and other ports that commonly need to be passed through firewalls and proxies.
- Application layer monitoring for P2P protocols can identify programs that use commonly allowed ports (53, 80). However, it fails when more malicious programs encrypt the payload.
- Some host based intrusion prevention software and system change auditing tools can prevent the installation or execution of P2P applications along with other malware.
- Pattern matching / behavioral Intrusion Detection systems can identify potential P2P members. Patterns observed include frequency, timing and size of communication bursts.
- Scanning network and PC storage for content commonly downloaded by P2P users, including *.mp3, *.wma, *.avi, *.mpg, *.mpeg, *.jpg, *.gif, *.zip, *.torrent, and *.exe files.
- Changes in network performance may indicate exploding P2P usage, or malware infections.
- Some Firewalls and Intrusion Detection/Prevention products implement detection techniques to detect/prevent P2P traffic from entering or leaving the network.
- For Microsoft Windows machines, SMS can be used to scan for executables that are installed on workstations. Furthermore, administrators should limit permissions in order to prevent users from installing such software on their workstations.
- Compromised systems that have malware installed via P2P file sharing will display the same symptoms seen when other means of malware distribution are successful.
A2.4 How to Protect against P2P Software Vulnerabilities
- Standard users should not be permitted to install software. Restrict Administrative and Power User level privileges to support personnel acting in their support capacity. If a user must have Administrative or Power User privileges, create a separate account to be used for his/her daily office functions, Internet surfing and on-line communication.
- Use tools such as Microsoft DropMyRights for securing Web browsers and mail clients.
- In Active Directory environments, Software Restriction Group Policies can be used in order to block known types of binaries from execution.
- Educate users about P2P networks, the dangers of file sharing and company policy.
- Turn on Egress filtering to restrict any ports not required for business purposes, although as more P2P applications move to http and encryption, this will prove less effective.
- Monitor firewall and IDS logs.
- To reduce malware infections which can be spread through numerous applications, use enterprise-wide anti-virus and antispyware products and ensure that updates are performed daily.
- Use host-based firewalls in addition to perimeter firewalls. Windows XP and Windows 2003 include Windows firewall, which provides adequate protection if properly configured. A variety of third-party host based firewalls (ZoneAlarm, Sygate, Outpost) provide additional functionality and flexibility. Windows 2000, XP and 2003 systems can use IPSec policies in order to provide port filtering of unnecessary network traffic over VPN. In Active Directory environments, IPSec policies and Windows Firewall configuration (for Windows XP SP2 and Windows 2003 SP1) can be managed centrally through Group Policies.
- Disable the Simple File Sharing feature of Windows XP if not explicitly required. [Start - Settings -Control Panel - Folder Options - Tab View - Disable (uncheck) setting Use Simple File Sharing - Apply - OK. ]
- Monitor systems for presence of unknown executables and unauthorized modification of system files. Software products like Tripwire or AIDE (there are commercial and open source versions of the product) can be used to detect changes in files.
- Samba-based shares can be configured to run a filter upon opening or saving of files. A filetype detector and alerting system could prove useful to avoid misusage of shares.
A2.5 References
Wikipedia Peer-to-peer
http://en.wikipedia.org/wiki/Peer-to-peerStorm Worm
http://www.secureworks.com/research/threats/view.html?threat=storm-worm
http://en.wikipedia.org/wiki/Storm_botnetDepartment of Justice Cybercrime web site
http://www.usdoj.gov/criminal/cybercrimeOther software providers could be held secondarily liable for copyright infringement.
http://www.usdoj.gov/criminal/cybercrime/2006IPTFProgressReport(6-19-06).pdfFBI Education initiative
http://www.fbi.gov/cyberinvest/cyberedletter.htmThe Information Factories
http://www.wired.com/wired/archive/14.10/cloudware_pr.htmlMobile Service Clouds: A Self-managing Infrastructure for Autonomic Mobile Computing Services
http://www.cse.msu.edu/~farshad/publications/conferences/samimi06msc.pdfCyber Security Tip ST05-007 - Risks of File-Sharing Technology
http://www.us-cert.gov/cas/tips/ST05-007.htmlRisks of P2P File Sharing (Presentation)
http://www.ftc.gov/bcp/workshops/filesharing/presentations/hale.pdfSecuring Windows XP Professional in a Peer-to-Peer Networking Environment
http://www.microsoft.com/technet/security/smallbusiness/prodtech/windowsxp/sec_winxp_pro_p2p.mspxIdentifying P2P users using traffic analysis - Yiming Gong - 2005-07-21
http://www.securityfocus.com/infocus/1843Bot software looks to improve peerage
http://www.securityfocus.com/news/11390Stop the bots
http://www.securityfocus.com/columnists/398/1How to block specific network protocols and ports by using IPSec (MS KB article 813878)
http://support.microsoft.com/kb/813878Using Software Restriction Policies to Protect Against Unauthorized Software
http://www.microsoft.com/technet/prodtechnol/winxppro/maintain/rstrplcy.mspxAvailability and description of the Port Reporter tool (MS KB article 837243)
http://support.microsoft.com/kb/837243New features and functionality in PortQry version 2.0 (MS KB article 832919)
http://support.microsoft.com/default.aspx?kbid=832919Log Parser 2.2
http://www.microsoft.com/technet/scriptcenter/tools/logparser/default.mspxBrowsing the Web and Reading E-mail Safely as an Administrator (DropMyRights)
http://msdn2.microsoft.com/en-us/library/ms972827.aspxAmazon Cloud Computing goes beta
http://www.amazon.com/gp/browse.html?node=201590011Checkpoint Application Intelligence
http://www.checkpoint.com/products/downloads/applicationintelligence_whitepaper.pdfMicrosoft site search for peer-to-peer
http://search.msdn.microsoft.com/search/default.aspx?siteId=0&tab=0&query=peer-to-peerInstant-Messaging-and-P2P-Vulnerabilities-for-Health-Organizations
http://ezinearticles.com/?Instant-Messaging-and-P2P-Vulnerabilities-for-Health-Organizations&id=232800Detecting and Understanding Rootkits
http://www.buanzo.com.ar/sec/Rootkits.htmlApplication Layer Packet Classifier for Linux
http://l7-filter.sourceforge.net/Network Devices:
N1. VoIP Servers and Phones
N1.1 Description
Use of VoIP technologies has continued to expand during the past year. Rapid adoption to garner the economic advantages of VoIP has led many to overlook, or even set aside, security concerns. Vulnerabilities can exist throughout a VoIP network, from mismanaged and unpatched call proxy and media servers to the VoIP phones themselves. Vulnerabilities have been found in products such as Cisco Unified Call Manager and Asterisk, along with VoIP phones from multiple vendors. By leveraging those vulnerabilities, attackers can carry out VoIP phishing scams, eavesdropping, toll fraud, or denial-of-service attacks. Poorly designed implementations can provide inroads to data networks and researchers are continuing to uncover additional areas for potential attack, such as cross site scripting through VoIP clients.
As many VoIP servers -- especially the ones at VoIP service providers -- are an interface between SS7 (traditional phone signaling) and IP networks, an attacker capable of compromising a vulnerable VoIP server could potentially manipulate the SS7 signaling interconnection to disrupt services on the Public Switched Telephone Network (PSTN).
N1.2 CVE Entries
Asterisk
CVE-2007-1594, CVE-2007-1561Cisco Call Manager
CVE-2006-5277VoIP Phones
CVE-2007-4459, CVE-2007-2512, CVE-2007-3047, CVE-2007-2270, CVE-2006-7121, CVE-2007-0431, CVE-2006-6411, CVE-2006-5233, CVE-2006-5231, CVE-2006-5038Avaya
CVE-2007-5556Cisco IOS
CVE-2007-4291N1.3 How to Mitigate These VoIP Vulnerabilities
- Consider security concerns as an integral part of any VoIP implementation. Additional caution should be taken at the product selection phase to ensure the VoIP product vendors support OS patches as they are released. Many VoIP vendors will void support for unapproved patches and may take considerable time before approving them.
- Apply the vendor supplied patches for VoIP servers and phone software/firmware as they become available.
- Ensure that operating systems running VoIP servers are patched with the latest OS patch supplied by either the OS vendor or the VoIP product vendor.
- Scan the VoIP servers and phones to detect open ports. Firewall all the ports from the Internet that are not required for operation of the VoIP infrastructure.
- Use a VoIP protocol aware firewall or Intrusion Prevention product to ensure that all UDP ports on VoIP phones are not open to the Internet for RTP/RTCP communications.
- Disable all unnecessary services on phones and servers (telnet, HTTP etc.)
- Consider using VoIP protocol fuzzing tools such as OULU SIP PROTOS Suite against the VoIP components to ensure the VoIP protocol stack integrity.
- Apply separate VLANs to your voice and data network as much as your converged network will allow. Ensure that VoIP DHCP and TFTP servers are separate from your data network.
- Change the default passwords on phones' and proxies' administrative login functions.
- Ensure that the VoIP VLAN can not be used as a way to gain access to other core services, usually this is a propagated VLAN over different locations with some machines such as the Call Manager dual homed.
N1.4 References
Asterisk Security Advisories
http://www.asterisk.org/securityCisco Security Advisories and Notices
http://www.cisco.com/en/US/products/products_security_advisories_listing.htmlVoIP Security Alliance
http://www.voipsa.orgNIST 800-58: Security Considerations for VoIP Systems
http://csrc.nist.gov/publications/nistpubs/800-58/SP800-58-final.pdfZ1: Zero Day Attacks
Z1.1 Description
A zero day vulnerability occurs when a flaw in software code has been discovered and exploits of the flaw appear before a fix or patch is available. Once a working exploit of the vulnerability is released into the wild, users of the affected software will be compromised until a software patch is available or some form of mitigation is taken by the user. Several zero day attacks were recorded in 2007 although that number has dropped from the previous year. Mitigation and protection steps are explained later in this section.
Z1.2. Affected OSs
All operating systems and all software applications are vulnerable to zero day vulnerability discovery and exploitation.
Z1.3. CVE Entries
This past year several vulnerabilities had public exploits available before the official patch or remedy was issued. Some example CVE entries that reflect this trend are:
- Microsoft Office 2003 Brazilian Portuguese Grammar Checker CVE-2006-5574
- Microsoft Word CVE-2006-6456
- Microsoft Word CVE-2006-6561
- Microsoft Word CVE-2006-5994
- Microsoft Word CVE-2007-0515
- Windows Graphics Rendering Engine (ANI) CVE-2007-0038
- Windows DNS Server CVE-2007-1748
- Adobe Acrobat Reader plug-in CVE-2007-0045
- RealPlayer CVE-2007-5601
- Computer Associates BrightStor CVE-2007-1785
Z1.4. How to Protect against the vulnerabilities
Protecting against zero day vulnerability exploitation is a matter of great concern for most system administrators. To reduce the impact of a zero day attack, follow best business practices such as:
- Adopt a deny-all stance on firewalls and perimeter devices that protect internal networks
- Separate public-facing servers from internal systems
- Turn off unneeded services and remove user applications that do not support operational needs
- Follow the Principle of Least Privilege in setting user access controls, permissions, and rights
- Restrict or limit the use of active code such as Java script or ActiveX in browsers
- Educate users about opening unsolicited file attachments
- Disable the ability to follow links in email
- Disable the ability to automatically download images from the web in email
- Maintain an aggressive in-house security alerting and warning service (or outsource the capability) to become aware of zero-day exploits as they become public.
- Use end-point management solutions to rapidly issue patches or workarounds as they become available
- If you use Microsoft's Active Directory, take maximum advantage of Group Policy Objects to control user access
- Do not rely on anti-virus protection alone since zero-day attacks are often not detectable until new signatures are released
- Use third-party buffer overflow protection where possible on all systems
- Follow vendor recommendations on workarounds and mitigations until a patch is available
The Experts Who Helped Create The Top-20 2007 List
Project Director: Rohit Dhamankar, TippingPoint, a division of 3Com
Adam Safier, Global Systems & Strategies, Inc.
Alan Rouse, Security Architect, TANDBERG Television
Alan Paller, Director, SANS Institute
Alexander Kotkov, UBS Investment Bank
Amol Sarwate, Manager of Vulnerability Lab, Qualys
Andrew van der Stock, Director, OWASP
Anton Chuvakin, Director of Product Management @ LogLogic
Anthony Richardson, Monash University, Australia
Arturo "Buanzo" Busleiman - Consultor Independiente en Seguridad, Argentina
Cesar Tascon Alvarez, Deloitte, Spain
Christopher Rowe, Elon University
Craig Wright, BDO Kendalls, Australia
Dean Farrington
Donald Smith, Qwest
Ed Fisher, Ingersoll Rand
Edward Ray, Getronics
Ed Skoudis, Intelguardians
Dr. Eric Cole
Gerhard Eschelbeck, CTO, Webroot
Giuseppe Gottardi, Senior Security Engineer, Communication Valley S.p.a, Italy
Jean-Francois Legault, Deloitte & Touche LLP
Jeff Pike, Integrated Team Solutions Facility
Jeremian Grossman, OWASP
John-Thomas Gaietto
John Tannahill, J.Tannahill & Associates
Johannes Ullrich, Internet Storm Center, SANS
Jonathan Rubin, Dominion
Kevin Hong
Koon Yaw Tan, Monetary Authority of Singapore
Leo Pastor, Advanced Consulting and Training, Argentina and Brazil
Marcos A. Ferreira Jr., NX Security, Brazil
Marcus Sachs, SRI International and Internet Storm Center, SANS
Matteo Shea, Senior Security Engineer, Communication Valley S.p.a, Italy
Michel Cusin, Bell Canada
Michele Guel, Cisco Systems
Miguel Guirao A, Telcel
Naoshi Matsushita, NRI Secure Technologies
Olivier Devaux, Webroot
Pedro Bueno - McAfee AvertLabs and SANS Internet Storm Center
Ralf Durkee, Security Consultant
Rhodri Davies, Vistorm, UK
Rick Wanner, Technical Analyst, Corporate Security, SaskTel
Rob King, TippingPoint, a division of 3Com
Russ McRee, HolisticInfosec.org
Sandeep Dhameja, Trustwave
Syed Mohamed, Microland Ltd.
Tom Hallewell, Radio Free AsiaAgencies
Department of Homeland Security (DHS)
Computer Emergency Response Team (CERT)
National Infrastructure Security Coordination Centre (NISCC, UK)
Computer Emergency Response Team, CanadaBest Practices for Preventing Top 20 Risks
- Configure systems, from the first day, with the most secure configuration that your business functionality will allow, and use automation to keep users from installing/uninstalling software
- Use automation to make sure systems maintain their secure configuration, remain fully patched with the latest version of the software (including keeping anti-virus software up to date)
- Use proxies on your border network, configuring all client services (HTTP, HTTPS, FTP, DNS, etc.) so that they have to pass through the proxies to get to the Internet
- Protect sensitive data through encryption, data classification mapped against access control, and through automated data leakage protection
- Use automated inoculation for awareness and provide penalties for those who do not follow acceptable use policy.
- Perform proper DMZ segmentation with firewalls
- Remove the security flaws in web applications by testing programmers security knowledge and testing the software for flaws.
SANS Top-20 2007 Security Risks FAQ
By Rohit Dhamankar, Project Director
- For whom is the list written?
Over the past few years, it has become clear to me that the SANS Top-20 list is used by very diverse organizations. Some large organizations use the Top-20 list for double-checking their ongoing security efforts whereas some small organizations use this list exclusively to guide their entire vulnerability remediation effort. So, while creating the list, we tried to serve the diverse audiences.
- Is it still relevant to publish this document in 2007 for a year's worth of vulnerabilities?
Examining the following facts, the answer is a clear "yes".
- Internet scanning data shows that there are still systems facing the Internet that are not patched for vulnerabilities being exploited widely. I, for one, will give up working on this project when I no longer see any Blaster or Slammer worm events triggering on any IDS/IPS in the customer networks.
- Even if all the patches have been applied, there are still zero-days to deal with! This year's list includes a list of defenses for zero-days.
- Security professionals get so focused on the "challenge of the day" that they need reminders, from time to time, of the emerging threats so they can ask for resources to fight those new threats.
- Why do you call it the Top-20 when the number of actual vulnerabilities (CVE's) is much greater that 20?
-
- Life would be much simpler if one could list 20 critical CVE numbers and say that protecting against attacks using those vulnerabilities would make the Internet safe. The reality, we all know, is far from that. If one just takes the weekly onslaught of web application vulnerabilities for the past year, the number of critical vulnerabilities is well over 100! These are the vulnerabilities that result in hundreds of thousands of attempted web attacks every day. The Top-20 approach is to help people focus on "classes" of vulnerabilities being exploited, and provide guidance to the system administrators, programmers, and CIOs on how to mitigate each class of flaws.
- The Top-20 groups critical vulnerabilities into classes so that common mitigation strategies can be applied to protect from an entire class. For instance, a large number of MS-RPC overflows can be prevented by blocking the ports 139/tcp and 445/tcp at the network perimeter.
- The Top-20 also helps identify the propagation vectors used by a large number of malware. It is still sad to see in 2007 malware successfully propagating in networks by brute-forcing passwords!
- We have retained the name "Top-20" to retain the brand that has been established for continuing work on this project.
If you have any comments, please write back to top20@sans.org
- Symantec Veritas Backup Exec
Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC

Check Them Out!
This is hands-down, the premiere training opportunity.
- Dan Mather, JICPAC


























